Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Descrição
In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.

Exploring Prompt Injection Attacks

Project Zero: Remote iPhone Exploitation Part 2: Bringing Light

Why Instagram Threads is a hotbed of risks for businesses

FastJSON deserialization bug can trigger RCE in popular Java

What is an Integer Overflow Attack (with Examples)?
Log4Shell Zero-Day Vulnerability - CVE-2021-44228

An Overview of MS-RPC and Its Security Mechanisms

An Overview of MS-RPC and Its Security Mechanisms
Sample Terms of Use Template and Guide - Termly
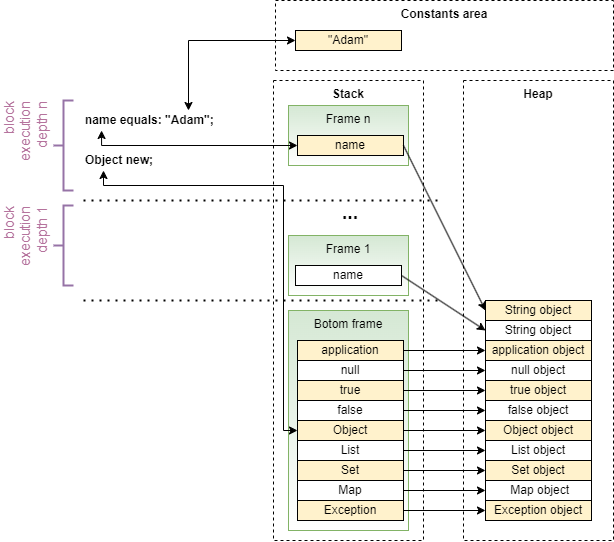
Smallscript - A Smalltalk-Inspired Scripting Language - CodeProject

How to protect, prevent and mitigate buffer overflow attacks

Cross-Sector Cybersecurity Performance Goals
de
por adulto (o preço varia de acordo com o tamanho do grupo)