Kung fu enumeration. Data collection in attacked systems – HackMag
Por um escritor misterioso
Descrição
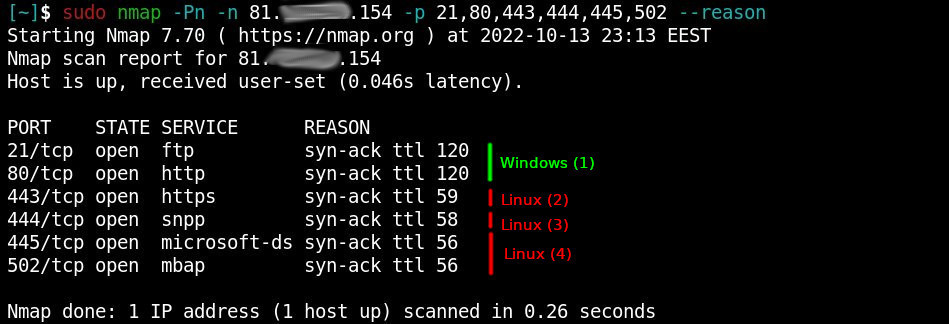
Kung fu enumeration. Data collection in attacked systems – HackMag

Black-box attacks and defense for DNN-based power quality

HACKMAGEDDON – Information Security Timelines and Statistics

Microsoft, hospital group use court order to disrupt ransomware

Xiangyu Qi - CatalyzeX
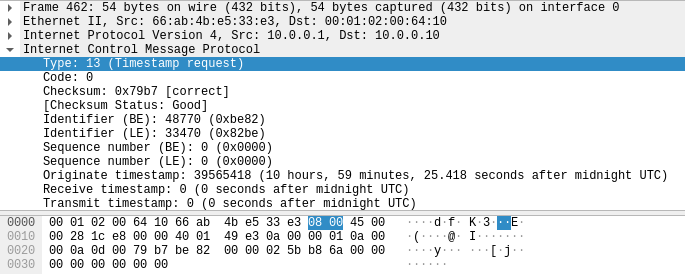
Kung fu enumeration. Data collection in attacked systems – HackMag

Hammond - Unit 17 Homework - GoodSecurity Penetration Test Report
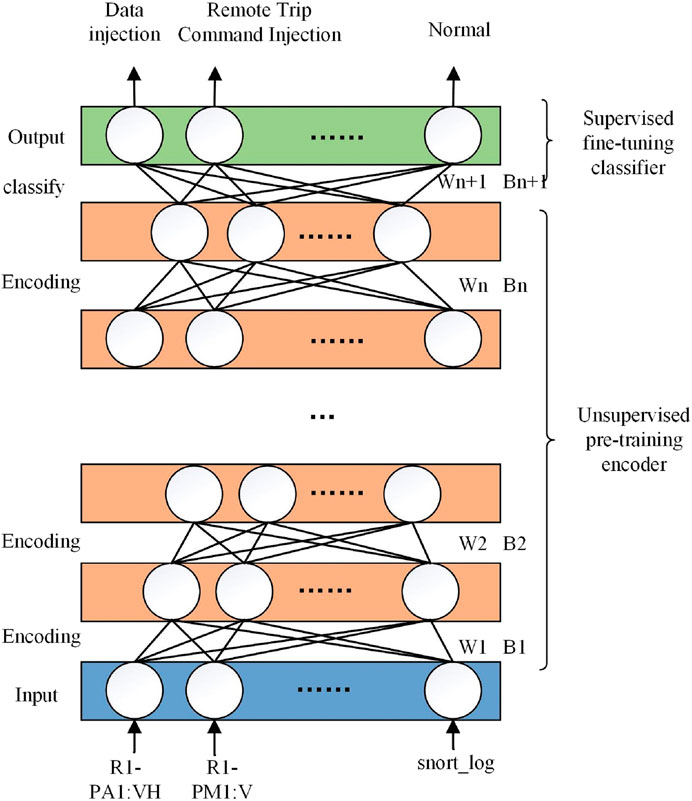
Frontiers False Data Injection Attack Detection in Power Systems
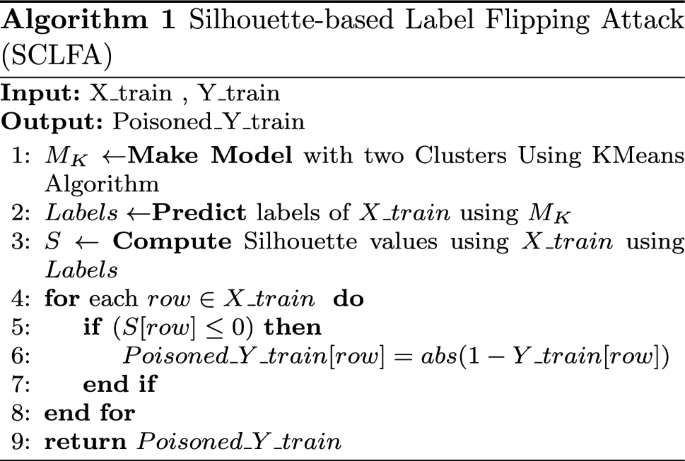
On defending against label flipping attacks on malware detection

Interview with one of the world's best competitive bug hunters
AppSec Ezines Url ( from
Kung fu enumeration. Data collection in attacked systems – HackMag
Find out if you have what it takes to keep the bad guys out of your network. This real-world resource contains 20+ hacking challenges for you to

Hacker's Challenge : Test Your Incident Response Skills Using 20 Scenarios

Data Injection Attack - an overview
de
por adulto (o preço varia de acordo com o tamanho do grupo)