Shellshock Vulnerability Exploitation and Mitigation: A Demonstration
Por um escritor misterioso
Descrição

About the Shellshock Vulnerability: The Basics of the “Bash Bug” - Security News
Shellshock Is Still a Risk, Even for Patched Machines

Malicious virtual machine configured as a router on a network whose

The ShellShock Vulnerability Explained

Presence of a poisoned DNS server on a network whose address is
Mitigating the Bash (ShellShock) Vulnerability - CrowdStrike
GitHub - pbr94/Shellshock-Bash-Remote-Code-Execution-Vulnerability-and- Exploitation

Exploiting and verifying shellshock: CVE-2014-6271
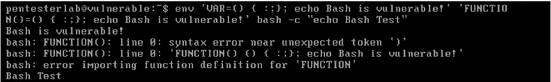
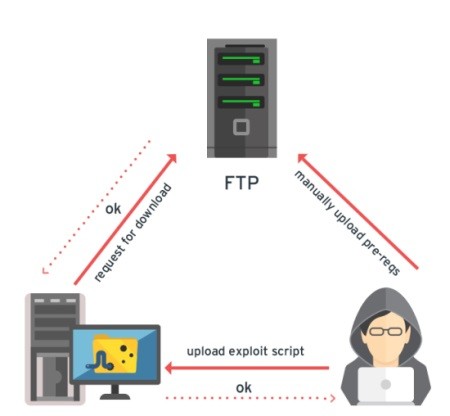
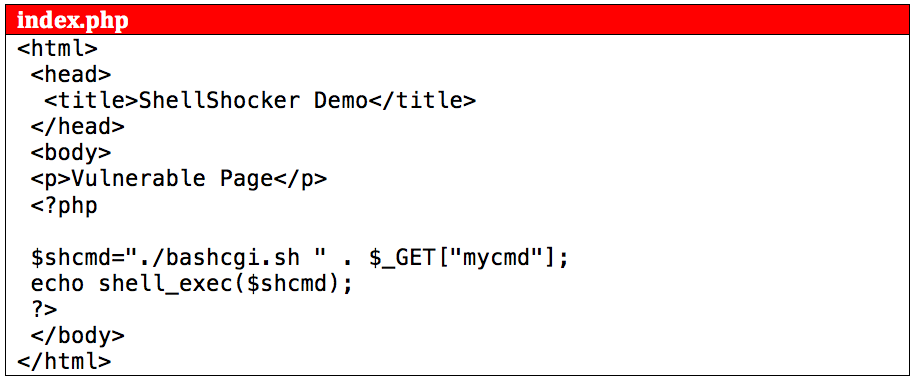
Shellshock Vulnerability Exploitation and Mitigation: A Demonstration

Shellshock Bash Bug Vulnerability Explained

What is Shellshock? This infographic explains how a Shellshock attack works and how to stay safe – Sophos News

What Is The Log4j Vulnerability And How To Mitigate It? • Scientyfic World
de
por adulto (o preço varia de acordo com o tamanho do grupo)







