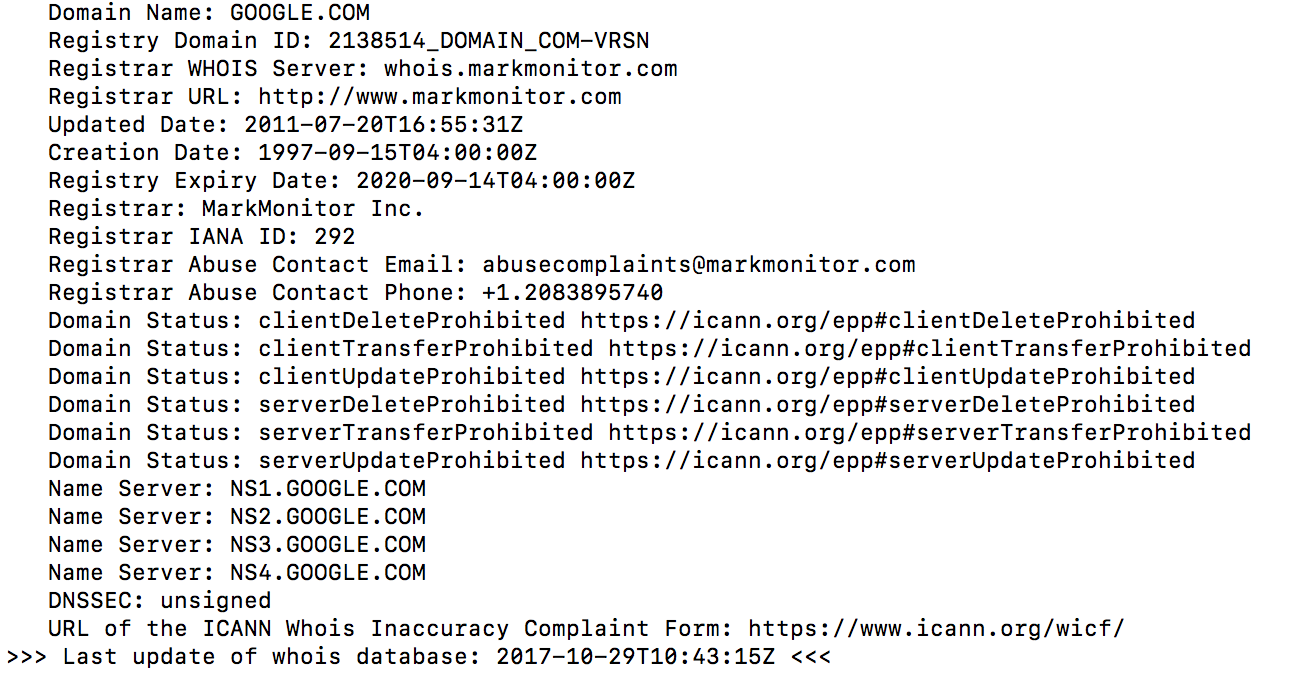
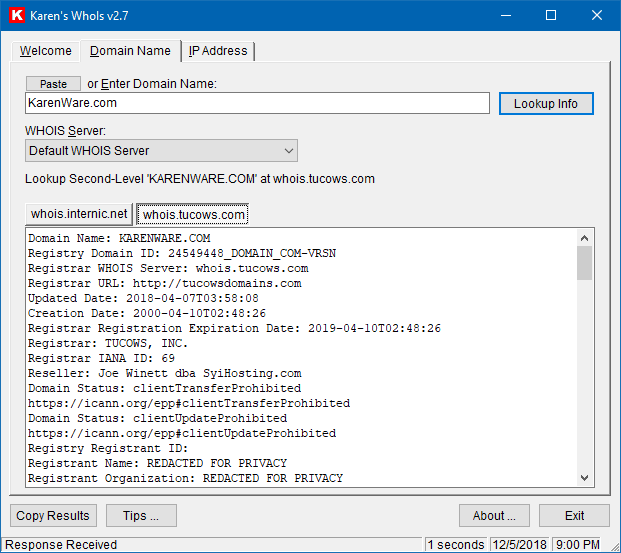
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Descrição
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

7 powerful pentesting tools (& why you should stop pedestalizing them)

Iranian Hackers Exploit PLCs in Attack on Water Authority in U.S.

Hackbun

Tips for Investigating Cybercrime Infrastructure
Ethical Hacking - How to start

Hezbollah's cyber unit hacked into telecoms and ISPs
Ronin Hack: North Korea's Lazarus Behind $540 Million Axe Infinity Breach

Certified Information Security And Ethical Hacker

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
de
por adulto (o preço varia de acordo com o tamanho do grupo)