Windows Command Shell — Malware Execution, by Kamran Saifullah
Por um escritor misterioso
Descrição
In my previous article I have talked about Windows Registry Keys i.e. what are they and how attackers/adversaries can alter their values in order to stay persistent and keep on doing what they want…

PDF) PROCEEDINGS BOOK OF THE 7th ADVANCED ENGINEERING DAYS 9 JULY 2023 / MERSIN, TURKEY

Kamran Saifullah – Medium
Windows Command Shell — Malware Execution, by Kamran Saifullah

PDF) Study of the Security Challenges for Industry 4.0

DevTunnels Unleashed

PDF) MOBILE GAME APPLICATION FOR STUDENT WITH LEARNING DISABILITIES TO IMPROVE UNDERSTANDING ON ADDITION AND SUBTRACTION OPERATION

CrashProcessUnit: Stack-based buffer overflow on Icarus Verilog

Analyzing Malicious PDF Files - GISPP - Global InfoSec Pakistani Professionals

Analyzing Malicious Word Documents - GISPP - Global InfoSec Pakistani Professionals
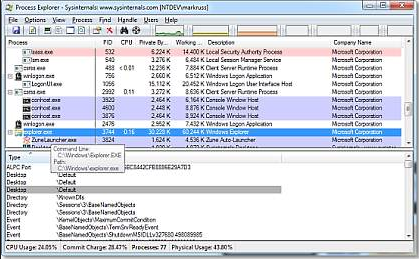
Malware Analysis — Part 2. In the first part, we discussed about…, by Akash Sarode
Kamran Saifullah 🇶🇦 (@deFr0ggy) / X
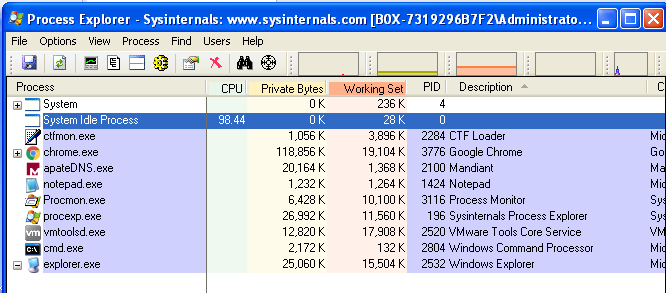
Practical Malware Analysis — Chapter 3 — Lab03–04 — Solution, by Kamran Saifullah
Sigma Rules List – VirusTotal

Window Privilege Escalation via Automated Script

Kamran Saifullah 🇶🇦 (@deFr0ggy) / X
de
por adulto (o preço varia de acordo com o tamanho do grupo)