Malware analysis Malicious activity
Por um escritor misterioso
Descrição

UK and allies support Ukraine calling out Russia's GRU for

Brute Force Attacks: Password Protection

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Malware Analysis: Steps & Examples - CrowdStrike

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus
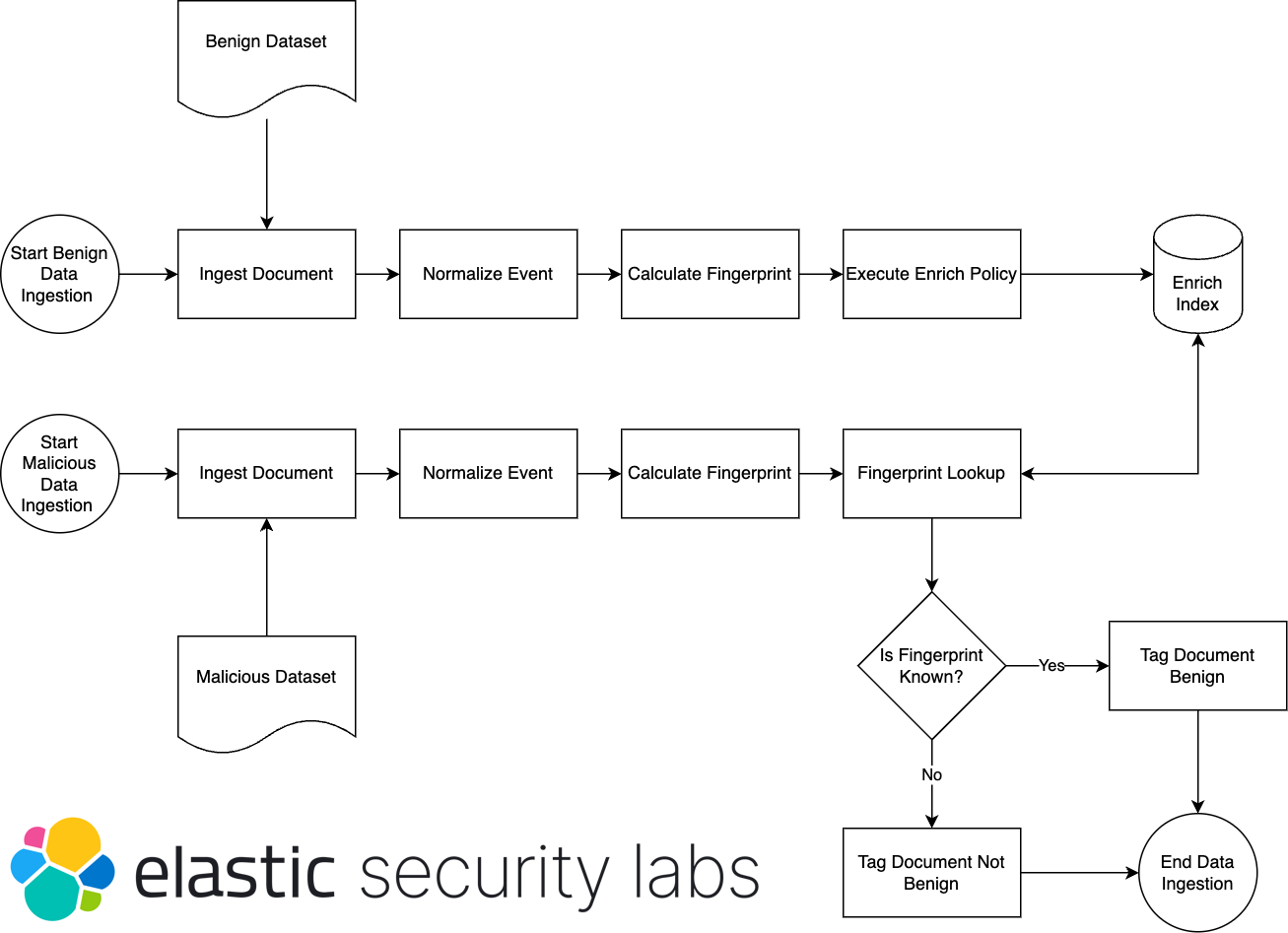
An Elastic approach to large-scale dynamic malware analysis — Elastic Security Labs

Malware analysis file Malicious activity
TryHackMe Hacktivities
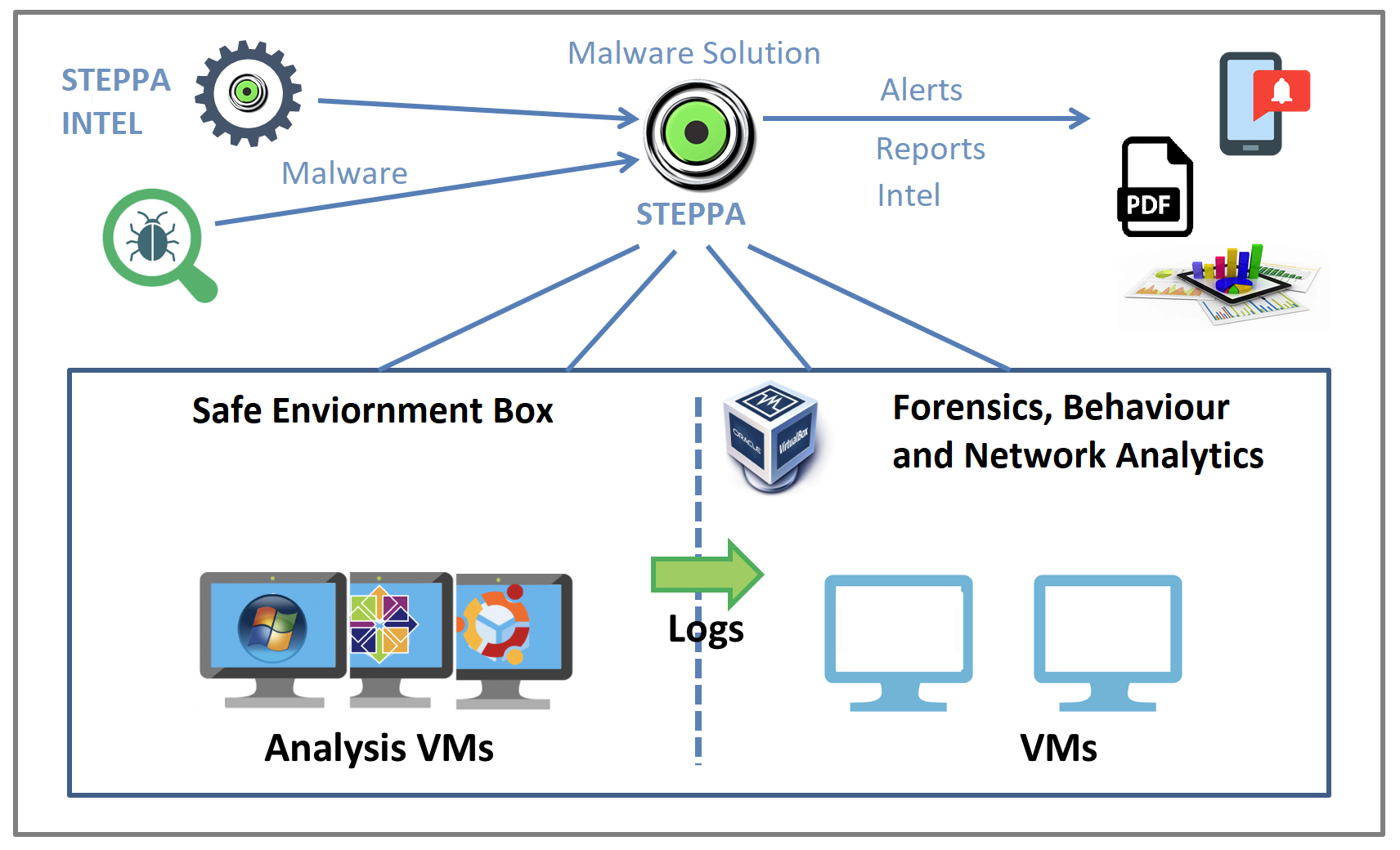
Malware Analysis Solution: Analyze, Detect, and Protect

ReversingLabs Malware Lab: Detect, classify, analyze, and respond to malicious files - Help Net Security
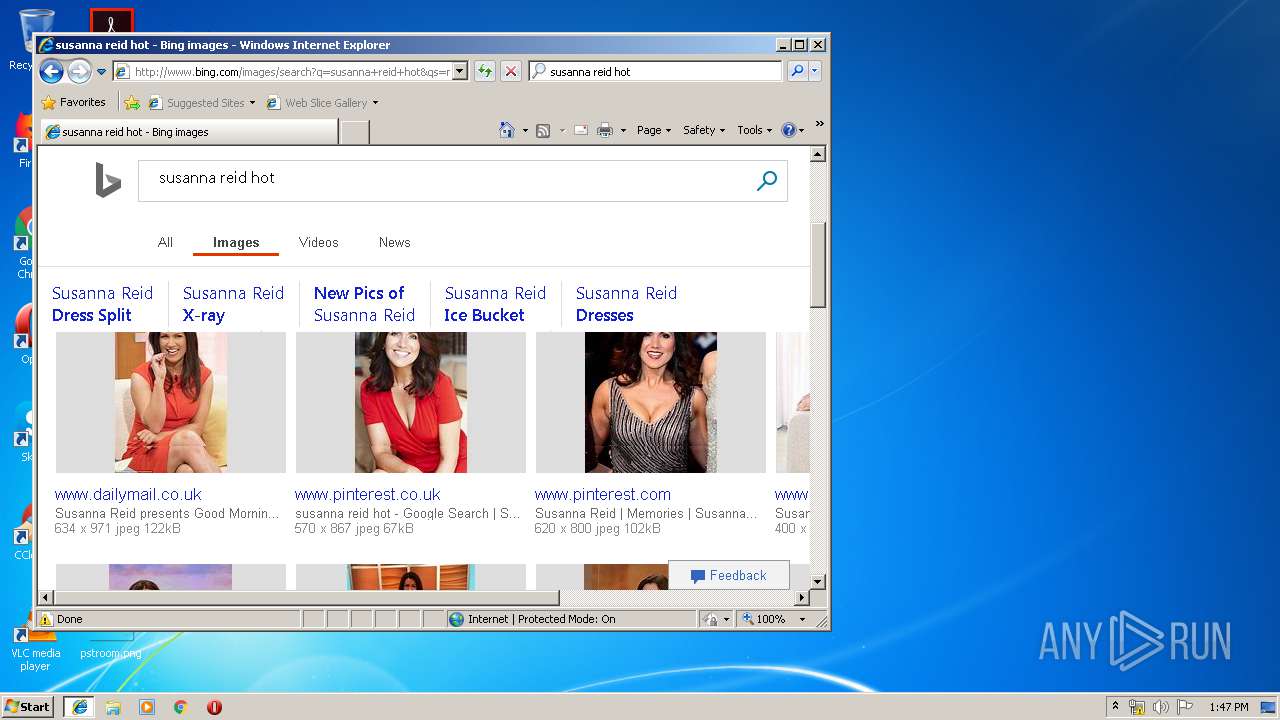
Malware analysis index.html Malicious activity

MetaDefender Cloud Advanced threat prevention and detection

Web injections are back on the rise: 40+ banks affected by new malware campaign

Mastering Malware Analysis
de
por adulto (o preço varia de acordo com o tamanho do grupo)