Malware analysis Suspicious activity
Por um escritor misterioso
Descrição
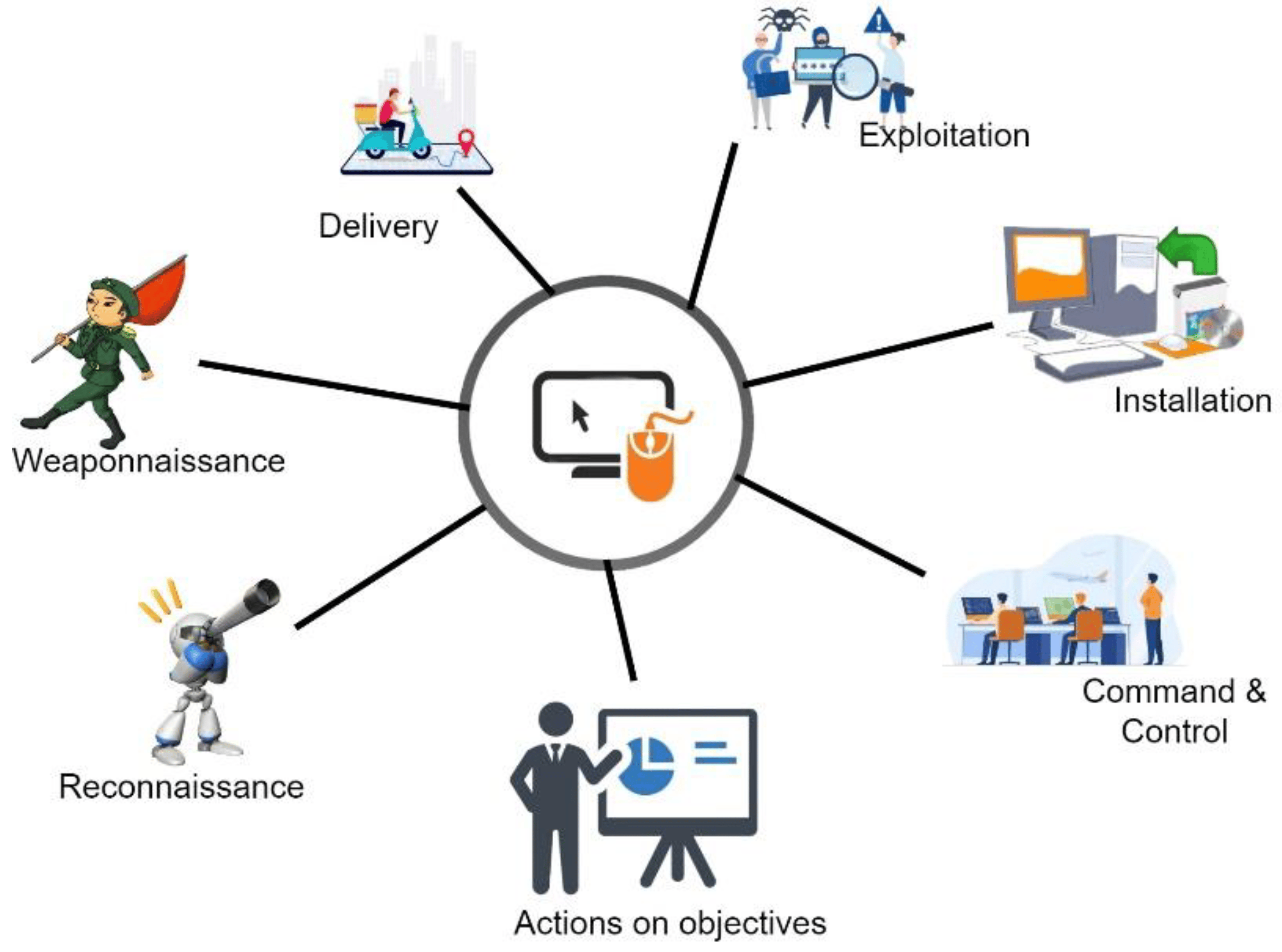
Symmetry, Free Full-Text

Malware Analysis Benefits Incident Response

Election Security Spotlight – Malware Analysis

Malware Analysis: Static vs. Dynamic and 4 Critical Best Practices
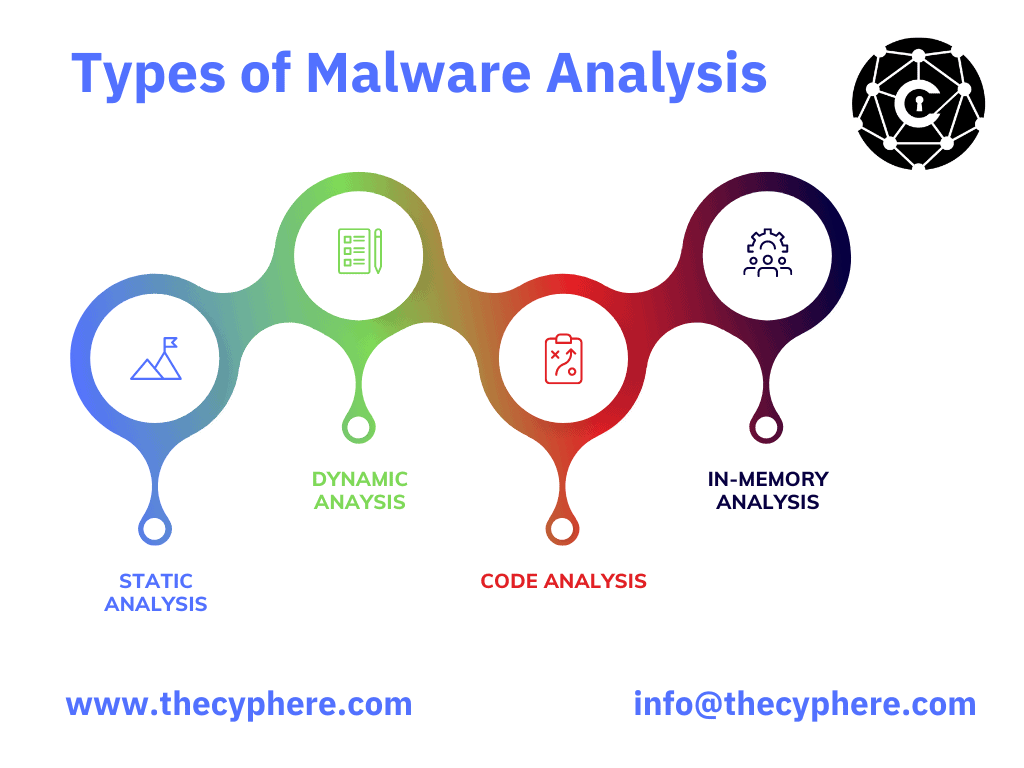
Malware Analysis Guide: Types & Tools
Top static malware analysis techniques for beginners
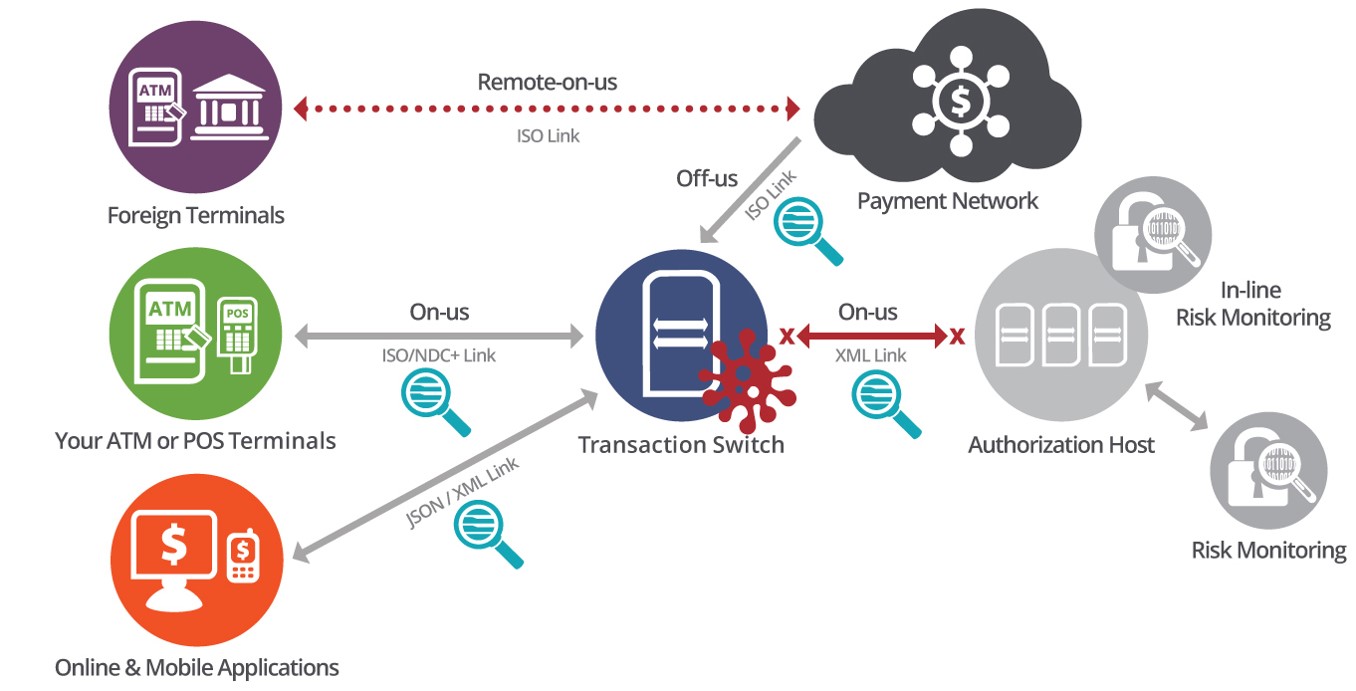
Malware Detection: One transaction at a time, INETCO Blog
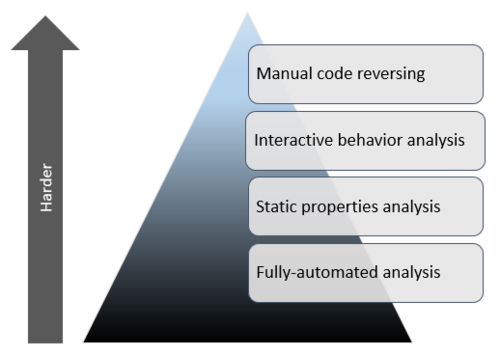
Mastering 4 Stages of Malware Analysis

Malware Analysis Tutorials: Complete Cheats Sheet - 2023

Ransomware: How it Works & How to Remove It

Malware Analysis: Steps & Examples - CrowdStrike

Behavioral blocking and containment: Transforming optics into
Monitoring for indicators of ransomware attacks - Splunk Lantern
de
por adulto (o preço varia de acordo com o tamanho do grupo)