Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing
Por um escritor misterioso
Descrição
Welcome to the new age of cyber attacks, where hackers have taken credential stuffing to the next level. Meet Credential Stuffing 2.0, where the use of proxies, CAPTCHA bypassing, CloudFlare security, and GUI tools have become the norm..
Cracking Tools that Automate Credential Stuffing & ATO

How Google Cloud can help stop credential stuffing attacks

How Credential Stuffing is Evolving - PasswordsCon 2019

10 Tips To Stop Credential Stuffing Attacks, by Jarrod Overson
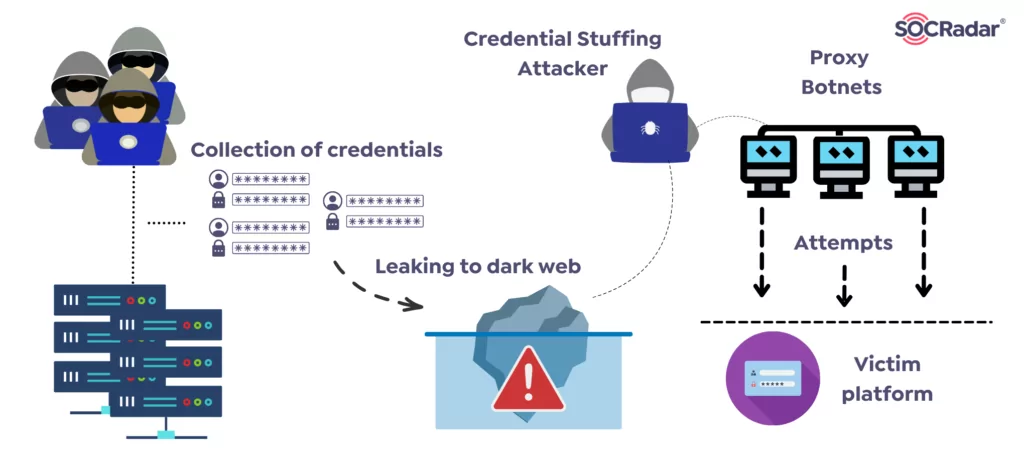
How to Prevent Credential Stuffing Attacks? - SOCRadar® Cyber Intelligence Inc.

How Google Cloud can help stop credential stuffing attacks
Credential stuffing attacks: How to protect your accounts from being compromised

How OpenBullet is used to attack websites, and how to block it.

Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing , CloudFlare Security, and GUI Tools

The State of Credential Stuffing and the Future of Account Takeovers.
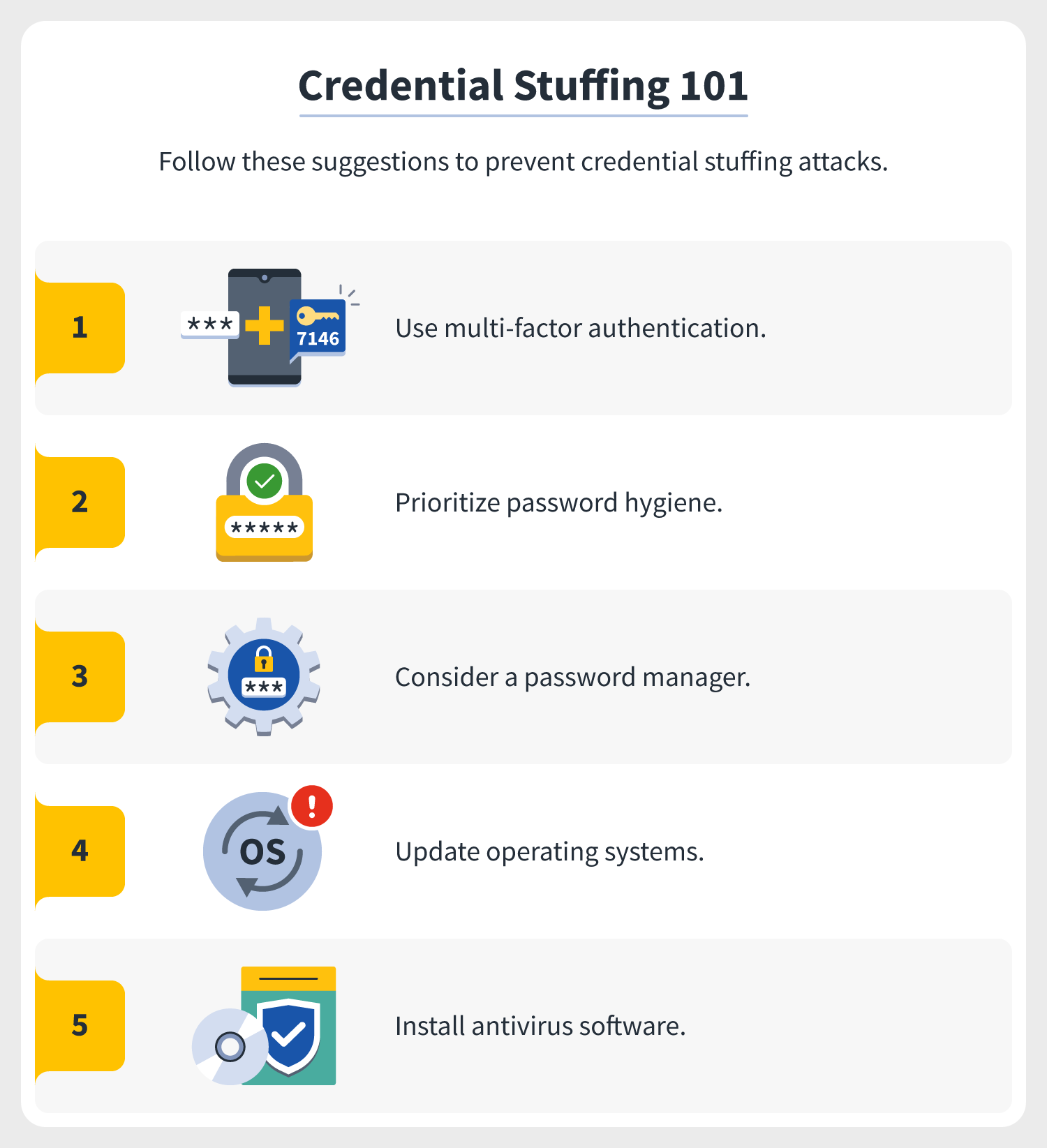
Credential stuffing simplified + attack protection tips
How to Bypass Cloudflare Bot Protection? Web Scraping Service in 2023

Email Compromise with Credential Stuffing Attack Tools
de
por adulto (o preço varia de acordo com o tamanho do grupo)