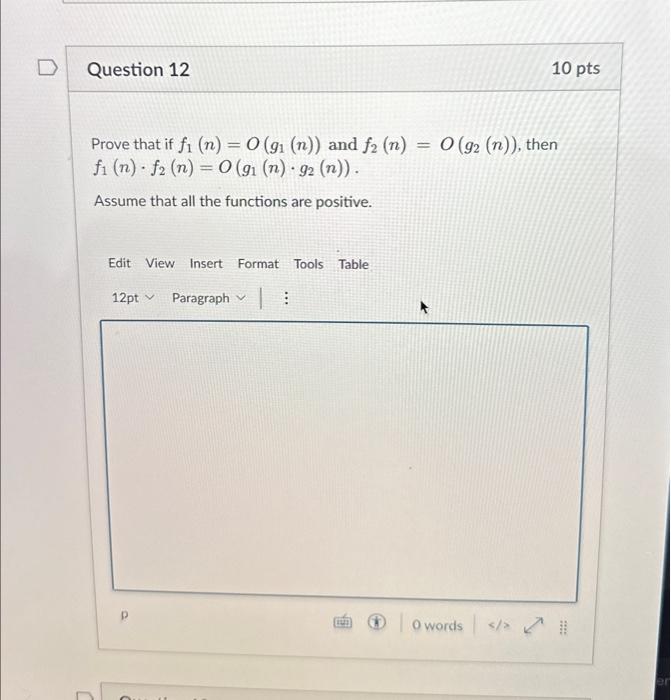
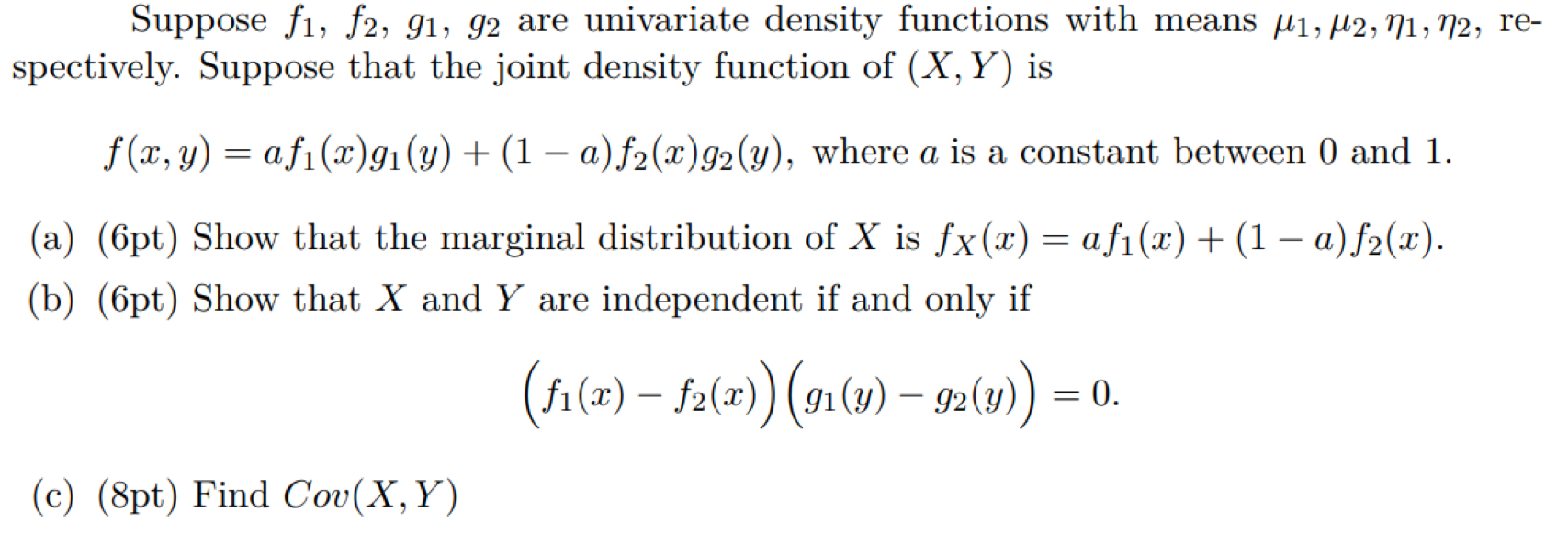
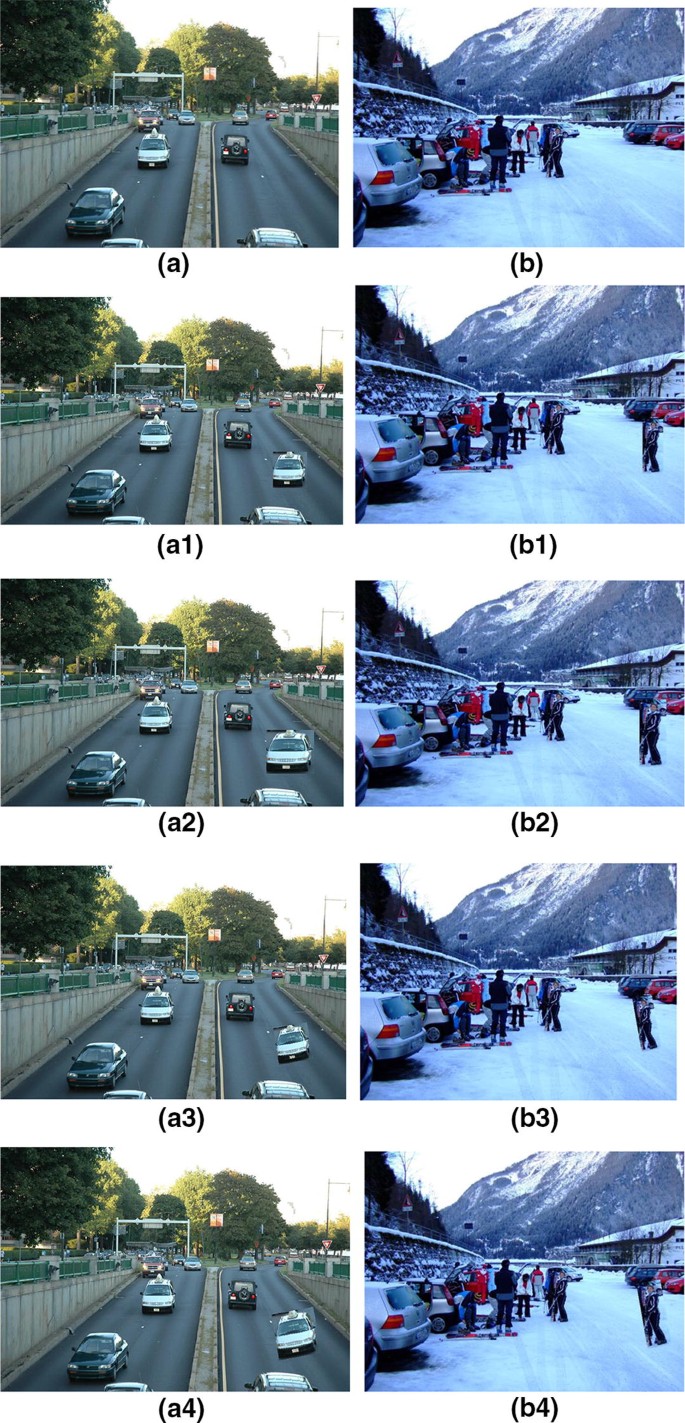
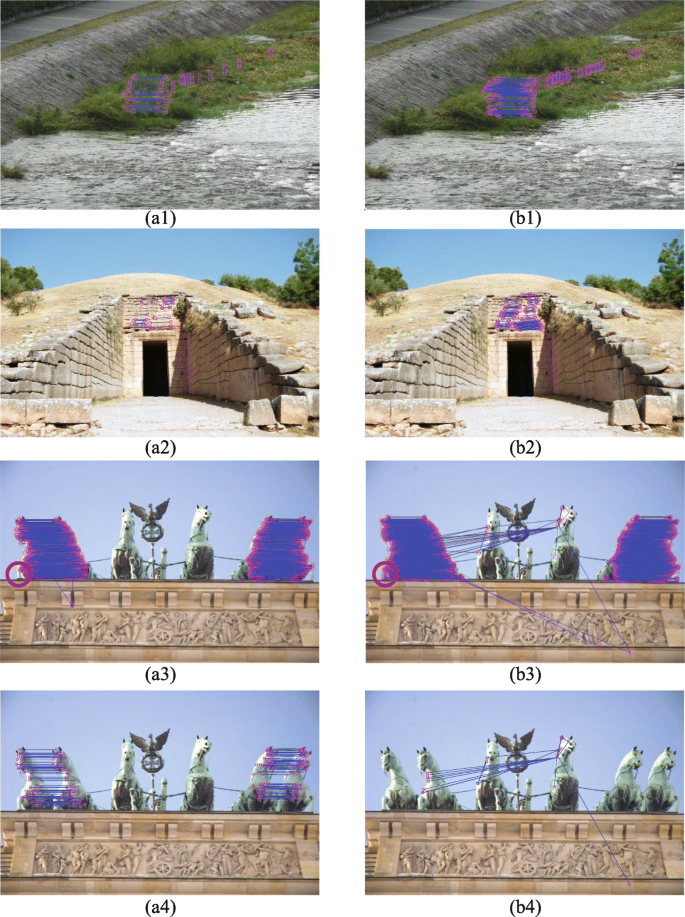
a1), {(b1)-(c1)}, (d1), (e1), and {(f1)-(g1)} shows copy-move forged
Por um escritor misterioso
Descrição
PDF) Detecting Copy move Forgery using DCT
Copy-Move Forgery Detection Based on Discrete and SURF Transforms

PDF] Copy-Move Forgery Detection Utilizing Local Binary Patterns
Copy-move image forgery detection based on evolving circular domains coverage

PDF] Copy-Move Forgery Detection Utilizing Local Binary Patterns
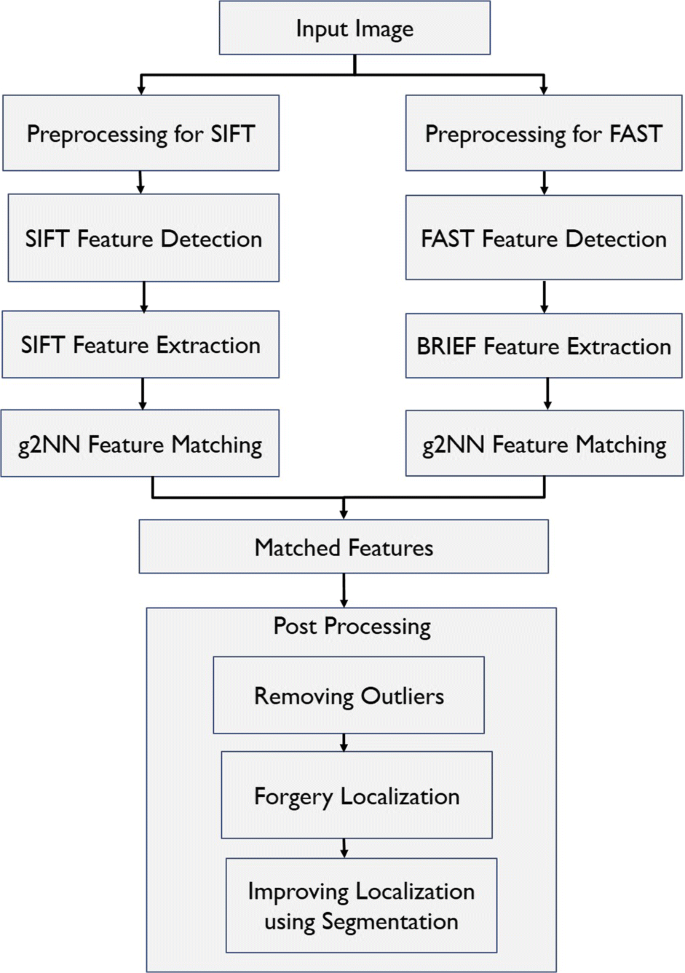
FAST, BRIEF and SIFT based image copy-move forgery detection technique

Robust dense‐field based copy‐move forgery localization using generic radial harmonic Fourier moment invariants - Atallah - Journal of Forensic Sciences - Wiley Online Library
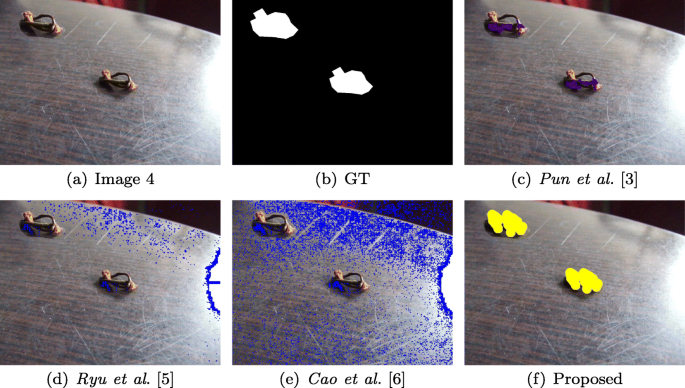
FAST, BRIEF and SIFT based image copy-move forgery detection technique

a1), (b1), (c1), (d1), (e1), and (f1) shows forged images with plain

Week 1 — Copy Move Forgery Detection, by Eflatun Doğa AYDIN, BBM406 Spring 2021 Projects
de
por adulto (o preço varia de acordo com o tamanho do grupo)