AiTM/ MFA phishing attacks in combination with new Microsoft protections (2023 edition)
Por um escritor misterioso
Descrição
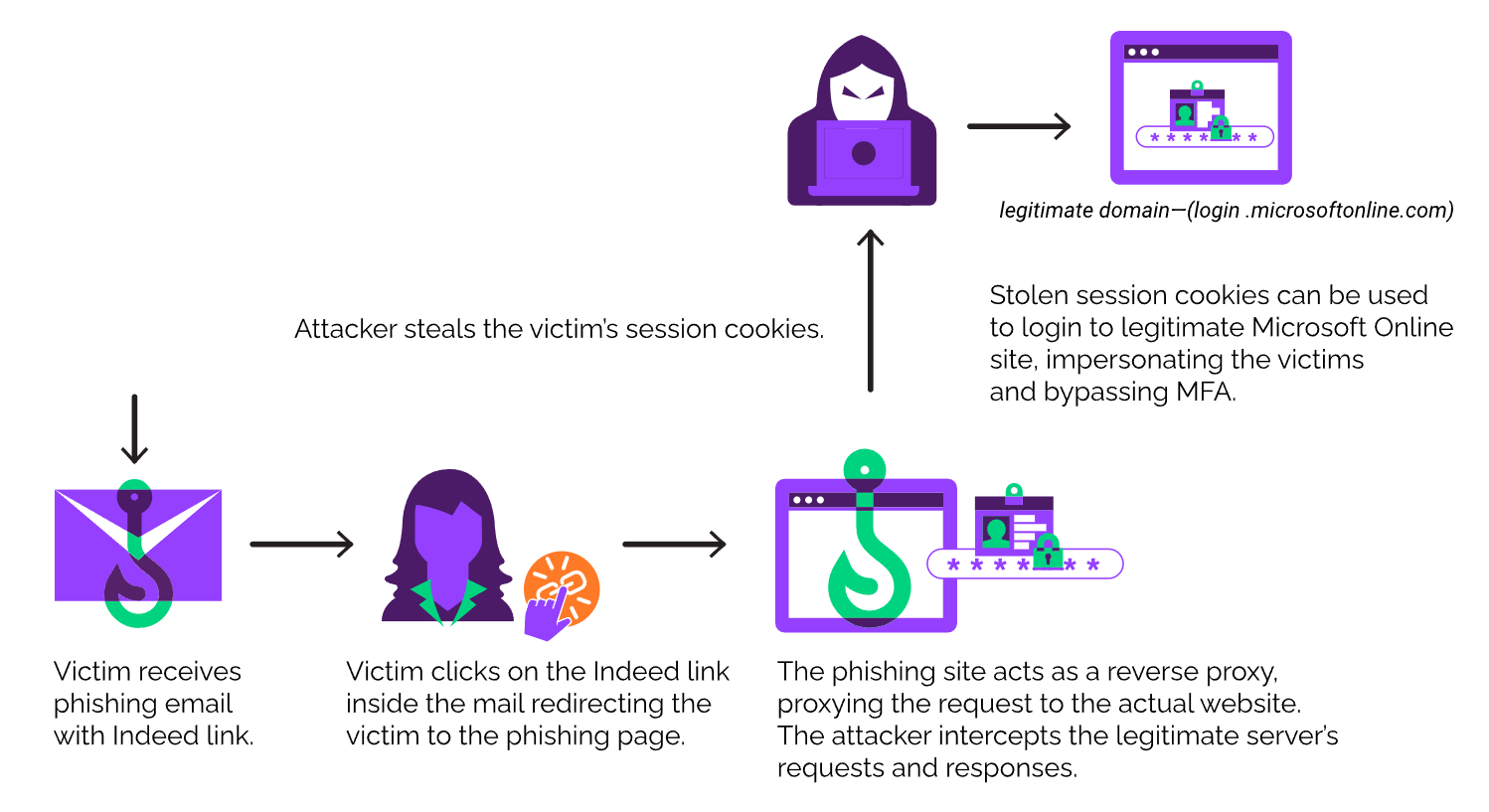
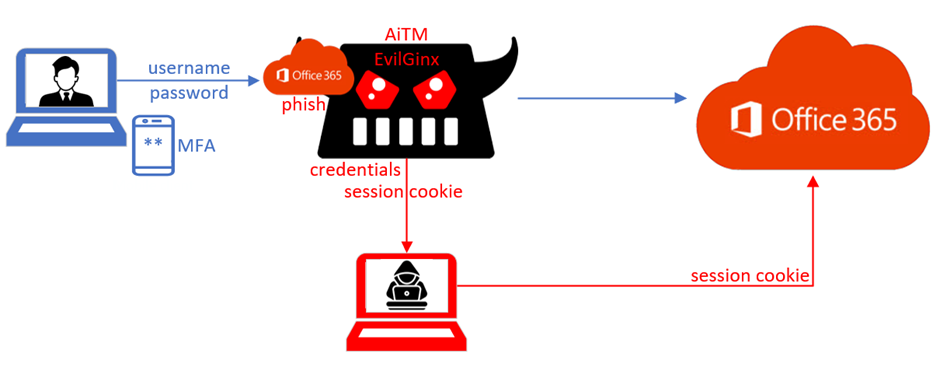
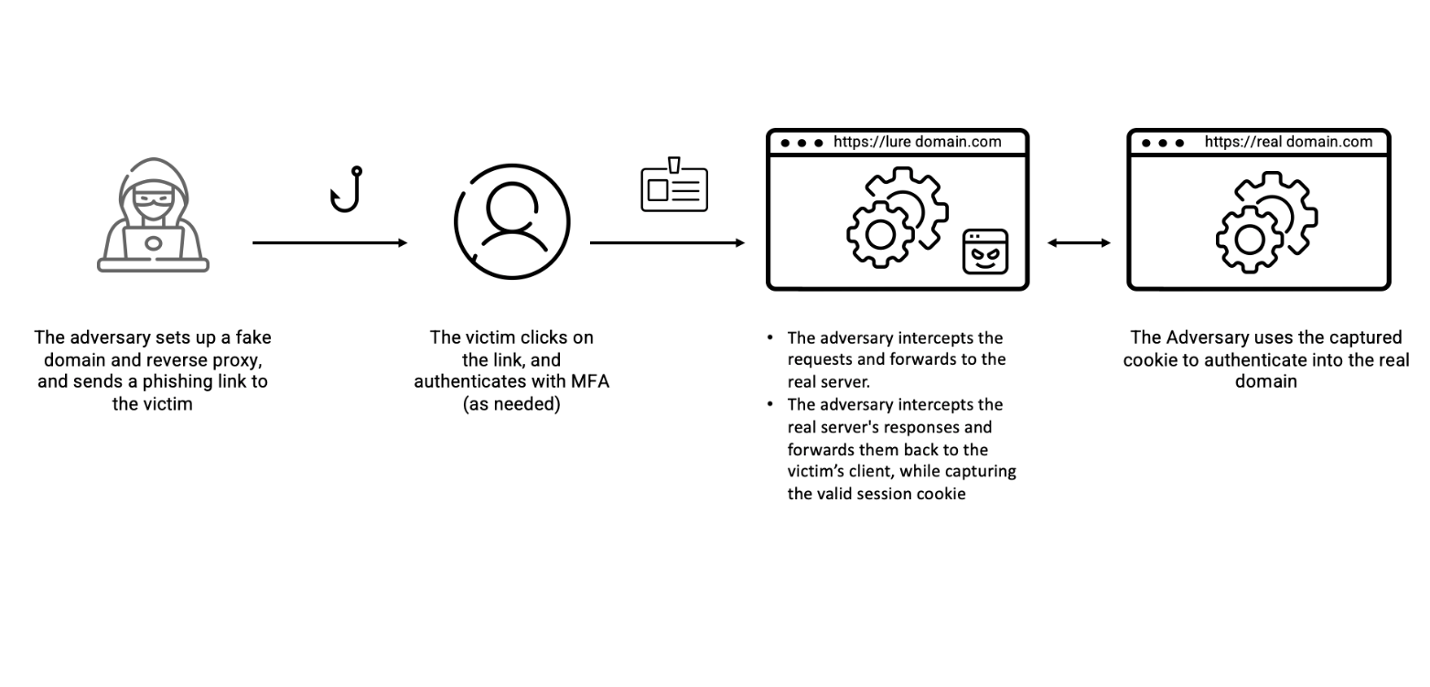
Adversary-in-the-middle phishing attacks are still more common in use. Since the removal of basic authentication from Exchange Online more and more attackers are using more modern attacks like adversary-in-the-middle phishing, cookie theft, and other used attacks. Last year I blogged about several modern
phishing Archives - Security Affairs
Detection Engineering Weekly #31 - MOVEit, get out the way
How to use Microsoft Entra, Internet Access to prevent AiTM attack(s), by Derk van der Woude

Phishing attacks bypassing MFA - Michigan SBDC

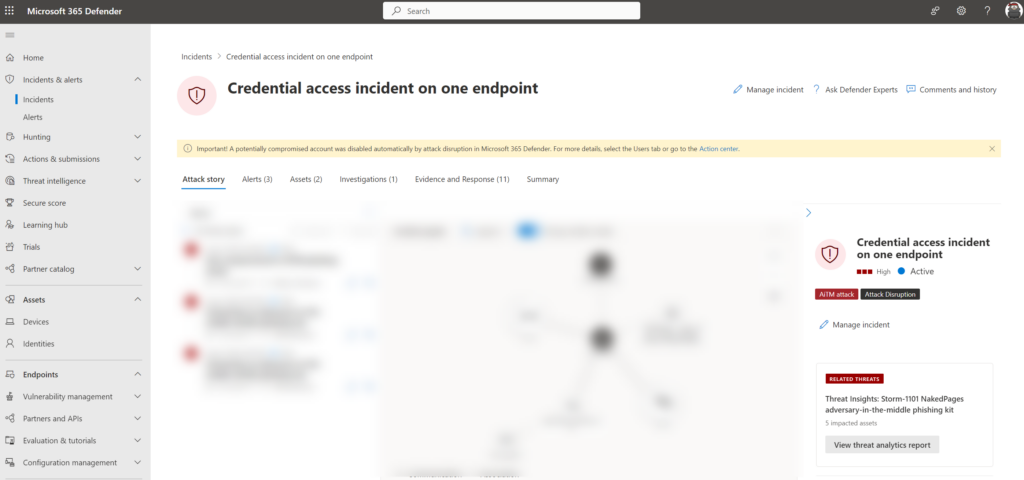
How to protect against BEC & AiTM attacks via Microsoft 365 Defender, Automatic Attack Disruption, by Derk van der Woude
EvilProxy Phishing Used for Cloud Account Takeover Campaign
AiTM/ MFA phishing attacks in combination with new Microsoft protections (2023 edition)

From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud

New AiTM Phishing Attack That Bypasses MFA Sets Sights On Microsoft Email Users

Detecting and mitigating a multi-stage AiTM phishing and BEC campaign
-1.png?width=600&height=401&name=Untitled%20design%20(5)-1.png)
AiTM phishing attacks: What to do when MFA is not enough

From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud

Pawel Partyka (@Pawp81) / X

AiTM Phishing Attack Chain Exploiting G-Suite Products
de
por adulto (o preço varia de acordo com o tamanho do grupo)