Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
Por um escritor misterioso
Descrição

TryHackMe : AOC 2022 [Day 12] Malware Analysis Forensic McBlue to the REVscue!, by JAMS_

Introducing VirusTotal Code Insight: Empowering threat analysis with generative AI ~ VirusTotal Blog
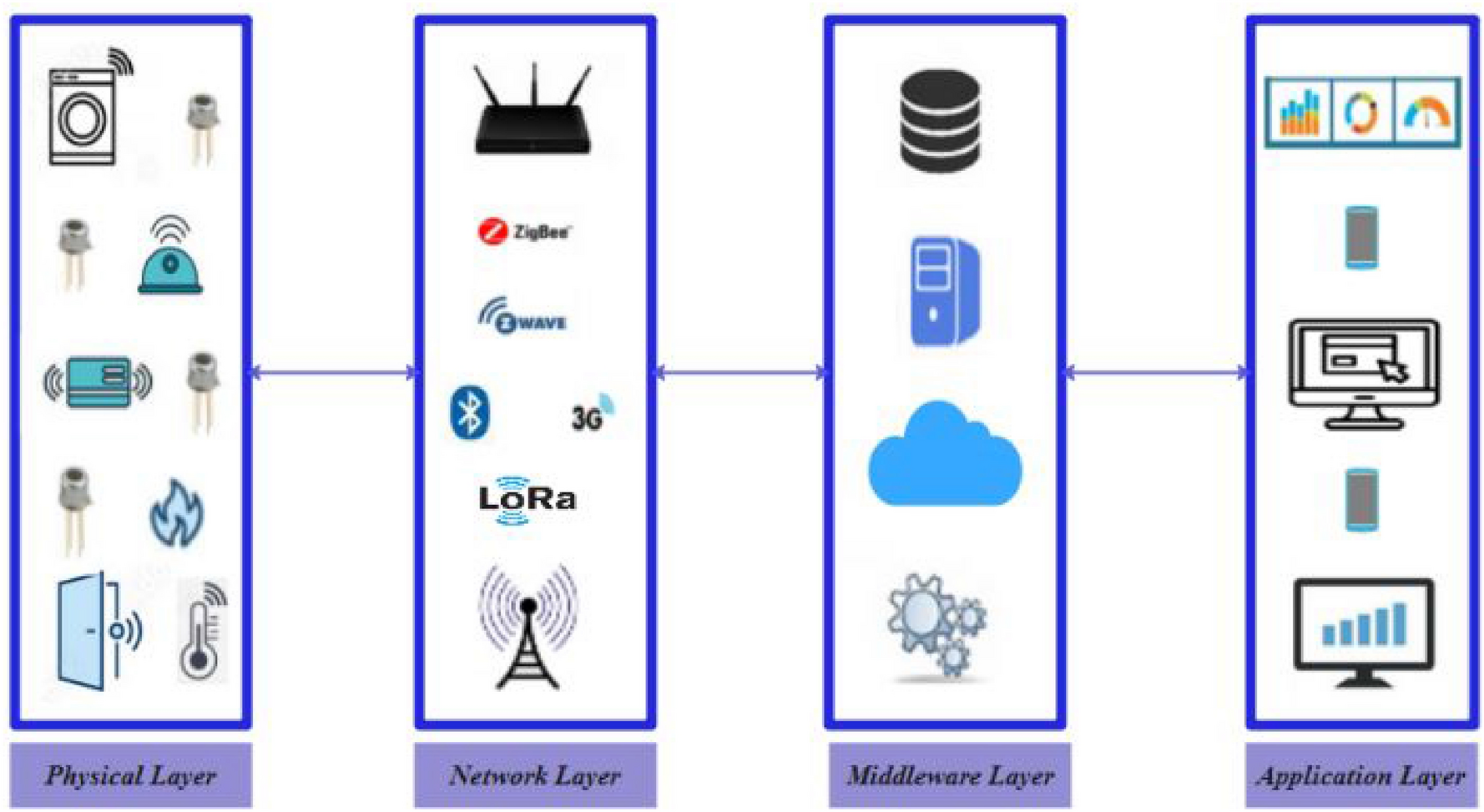
A survey on performance evaluation of artificial intelligence algorithms for improving IoT security systems
Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
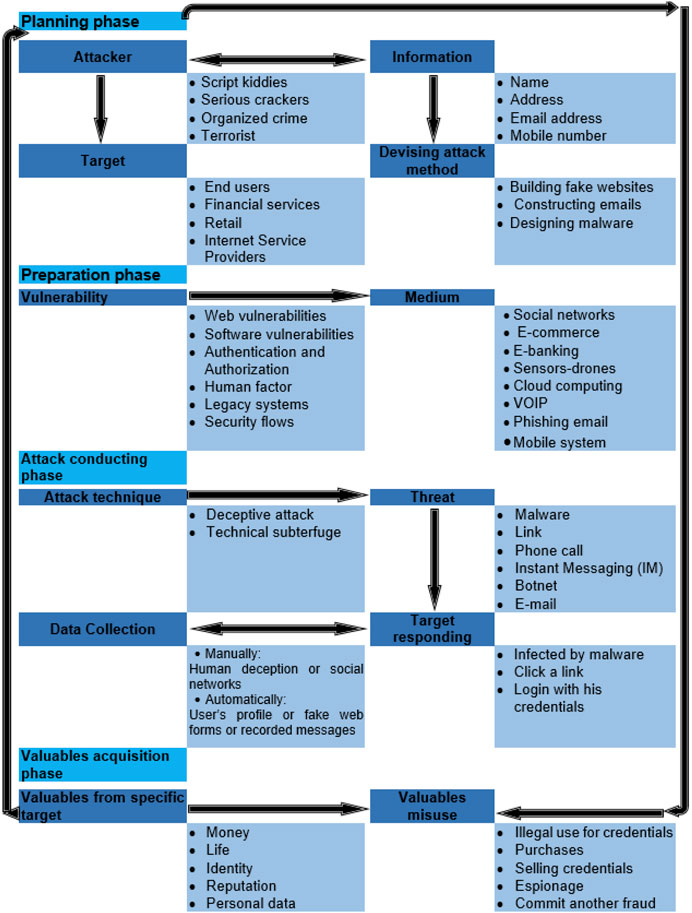
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy
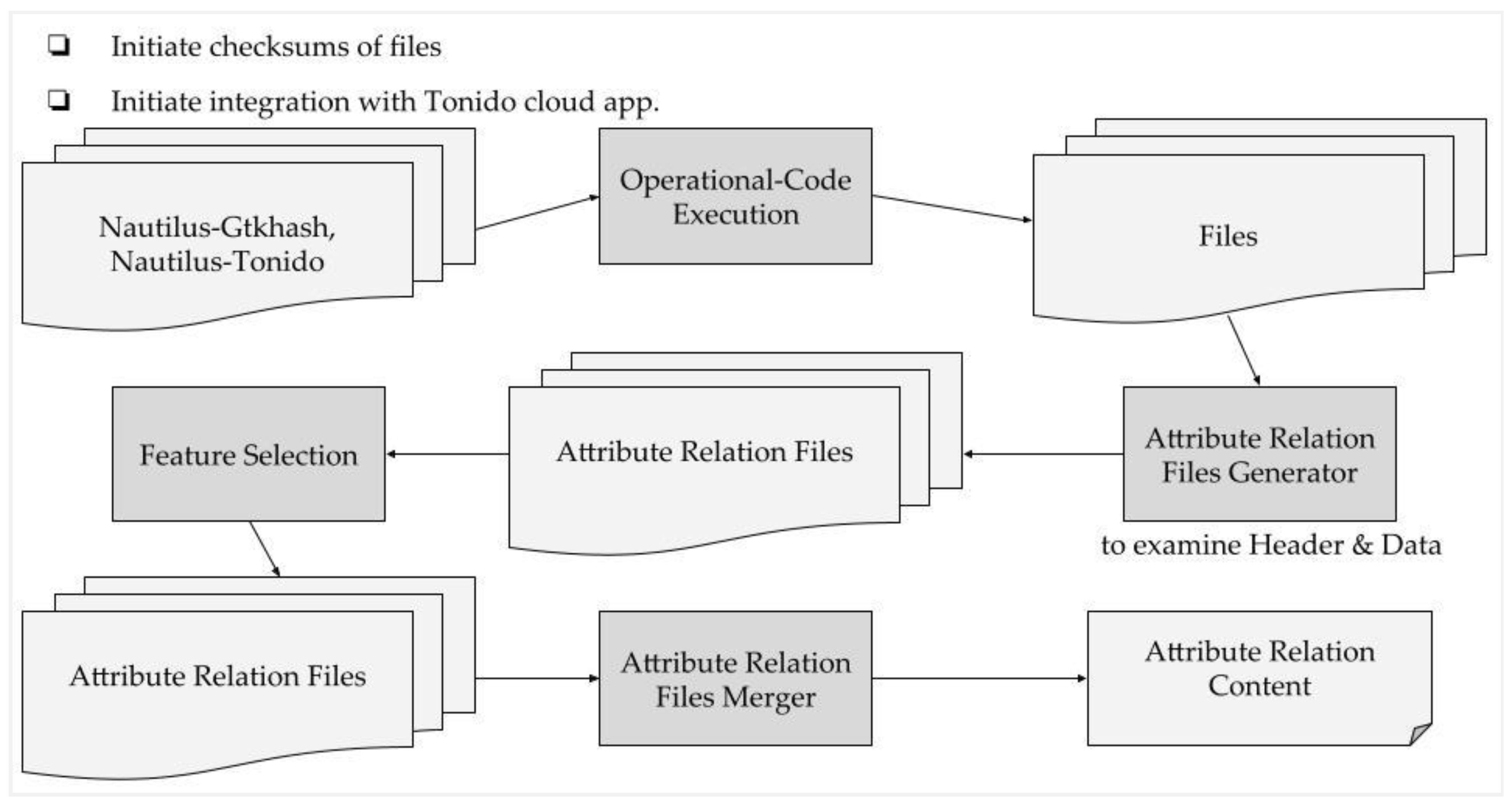
Mathematics, Free Full-Text

Exploring Prompt Injection Attacks, NCC Group Research Blog
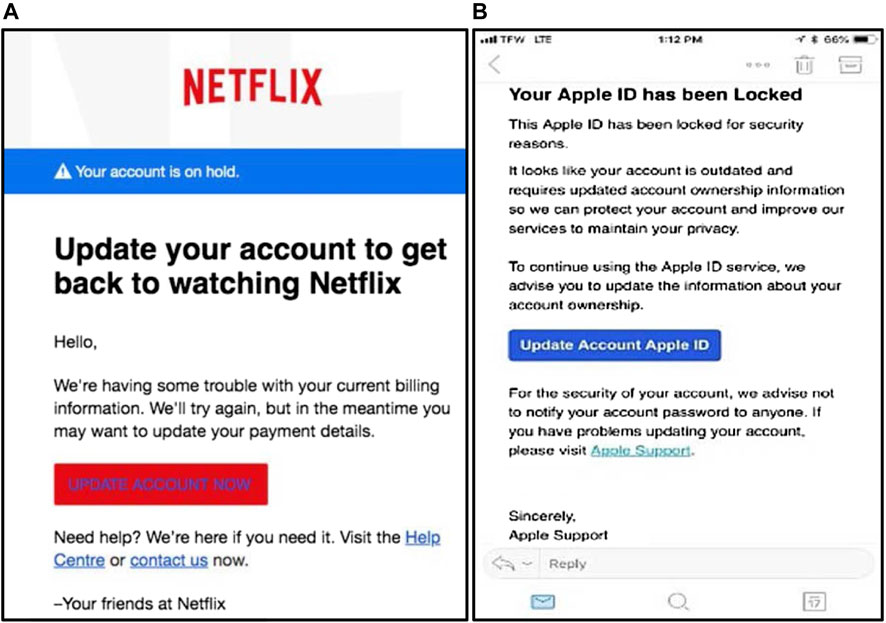
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy

Deep Learning for Zero-day Malware Detection and Classification: A Survey

Dave Greenfield, Author at Cato Networks

Disarming visualization-based approaches in malware detection systems - ScienceDirect
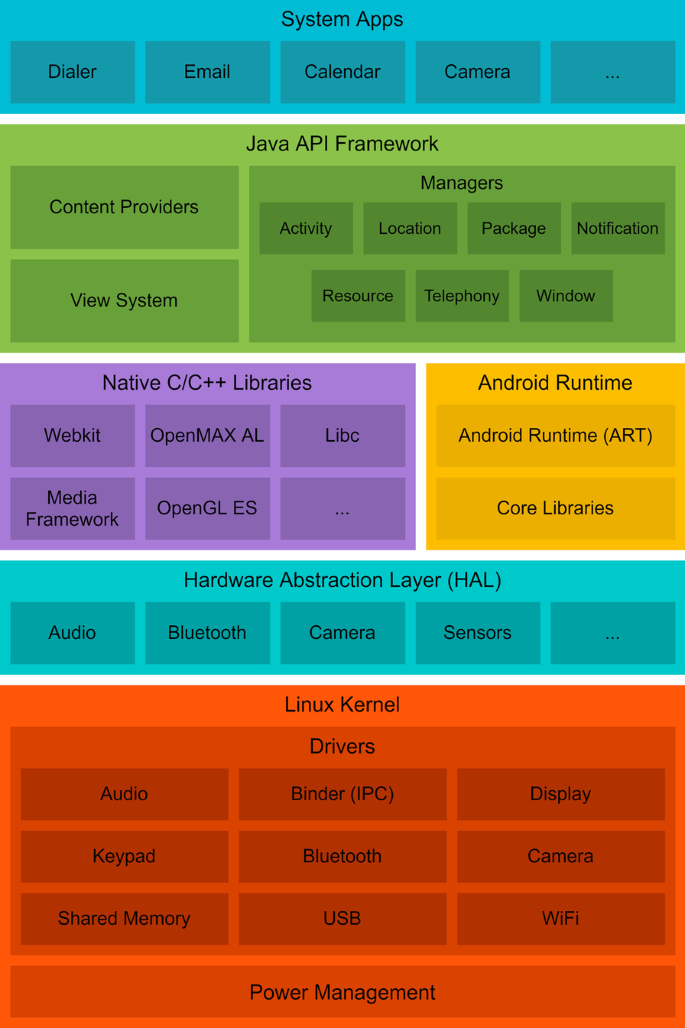
On building machine learning pipelines for Android malware detection: a procedural survey of practices, challenges and opportunities, Cybersecurity
de
por adulto (o preço varia de acordo com o tamanho do grupo)






