window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Descrição
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the

certificate - React Native Facebook Flipper Thread 9: EXC_BAD_ACCESS (code=1, address=0x201) - Stack Overflow

writeups/bug.md at main · tess-ss/writeups · GitHub

Comprehensive Guide on Open Redirect - Hacking Articles
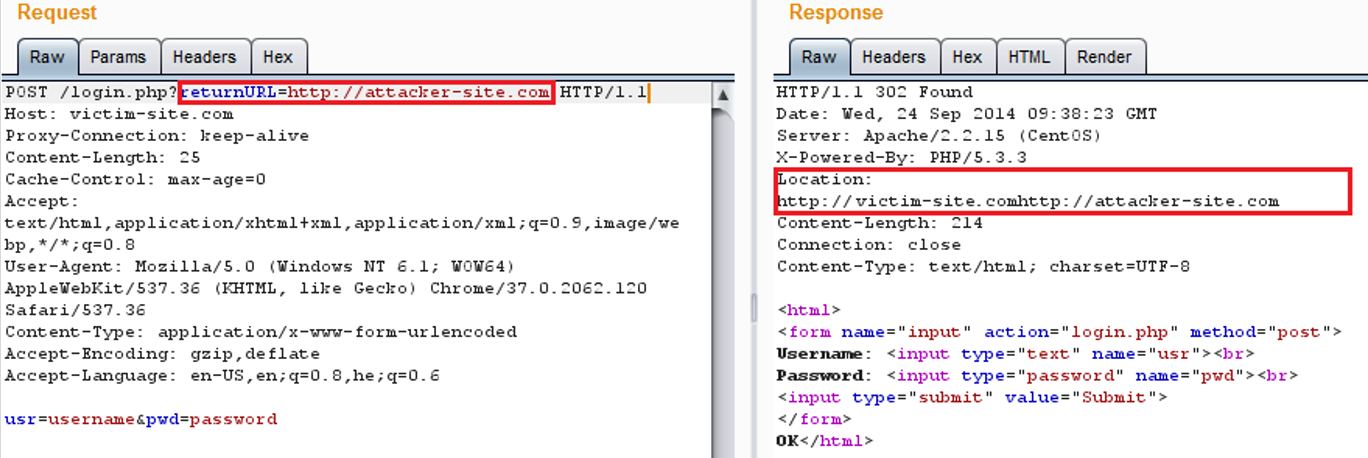
AppSec-Labs, Application Security

Turning Self-XSS into non-Self Stored-XSS via Authorization Issue at “PayPal Tech-Support and Brand Central Portal”, by YoKo Kho

writeups/bug.md at main · tess-ss/writeups · GitHub

Office 365 Hacked Using Google Open-Redirect Vulnerability
writeups/bug.md at main · tess-ss/writeups · GitHub
Warning] Stored XSS in TwoNav v2.0.28-20230624 · Issue #3 · tznb1/TwoNav · GitHub
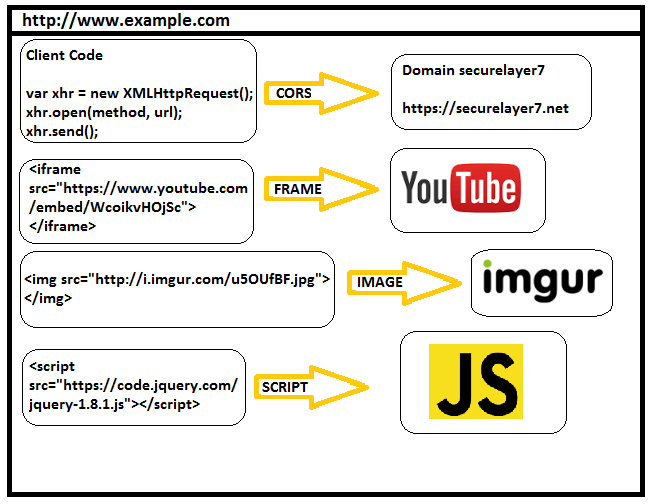
OWASP Top 10 : Cross-Site Scripting #3 Bad JavaScript Imports

Cross-site scripting (Practice on PortSwigger) - HackMD
de
por adulto (o preço varia de acordo com o tamanho do grupo)