Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Descrição
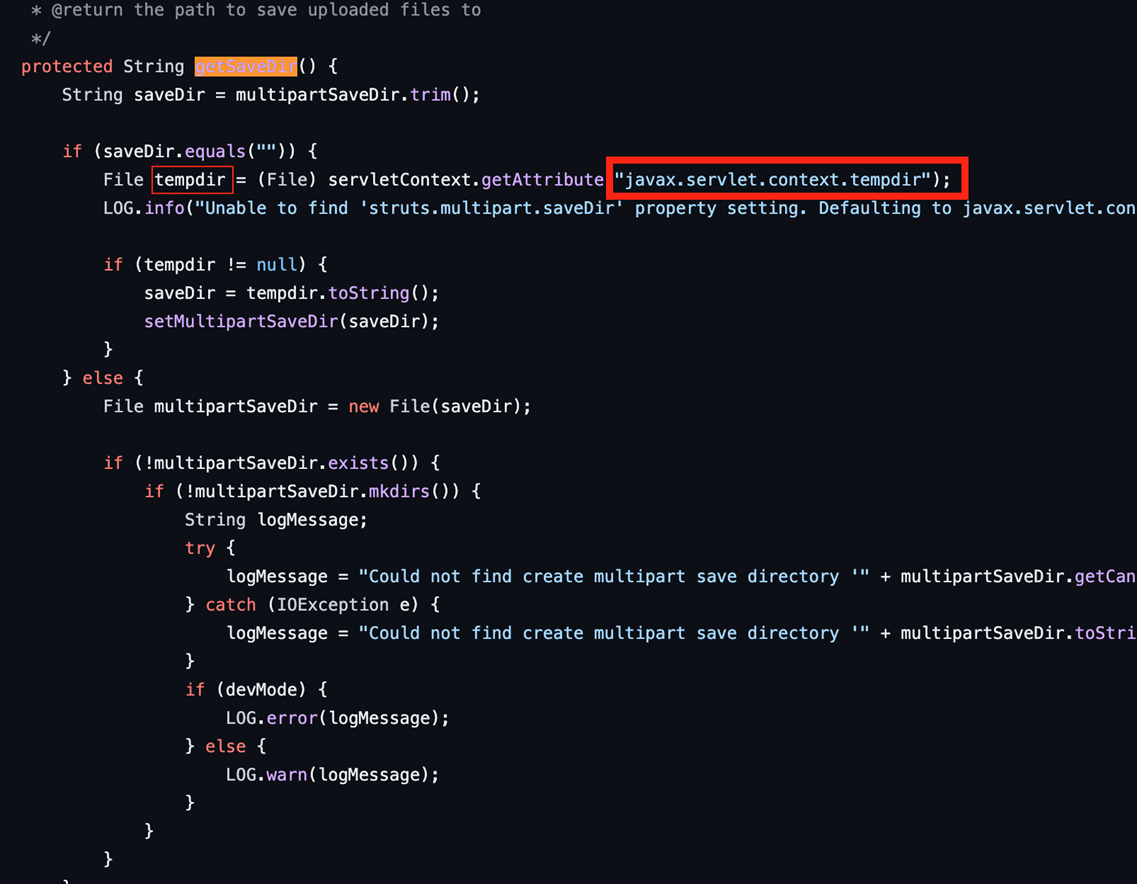
Decoding CVE-2023-50164: Unveiling the Apache Struts File Upload Exploit

100+ AI Use Cases & Applications: In-Depth Guide for 2023

Log Formatting: 7 Best Practices for Readable Log Files
Requesting website reclassification
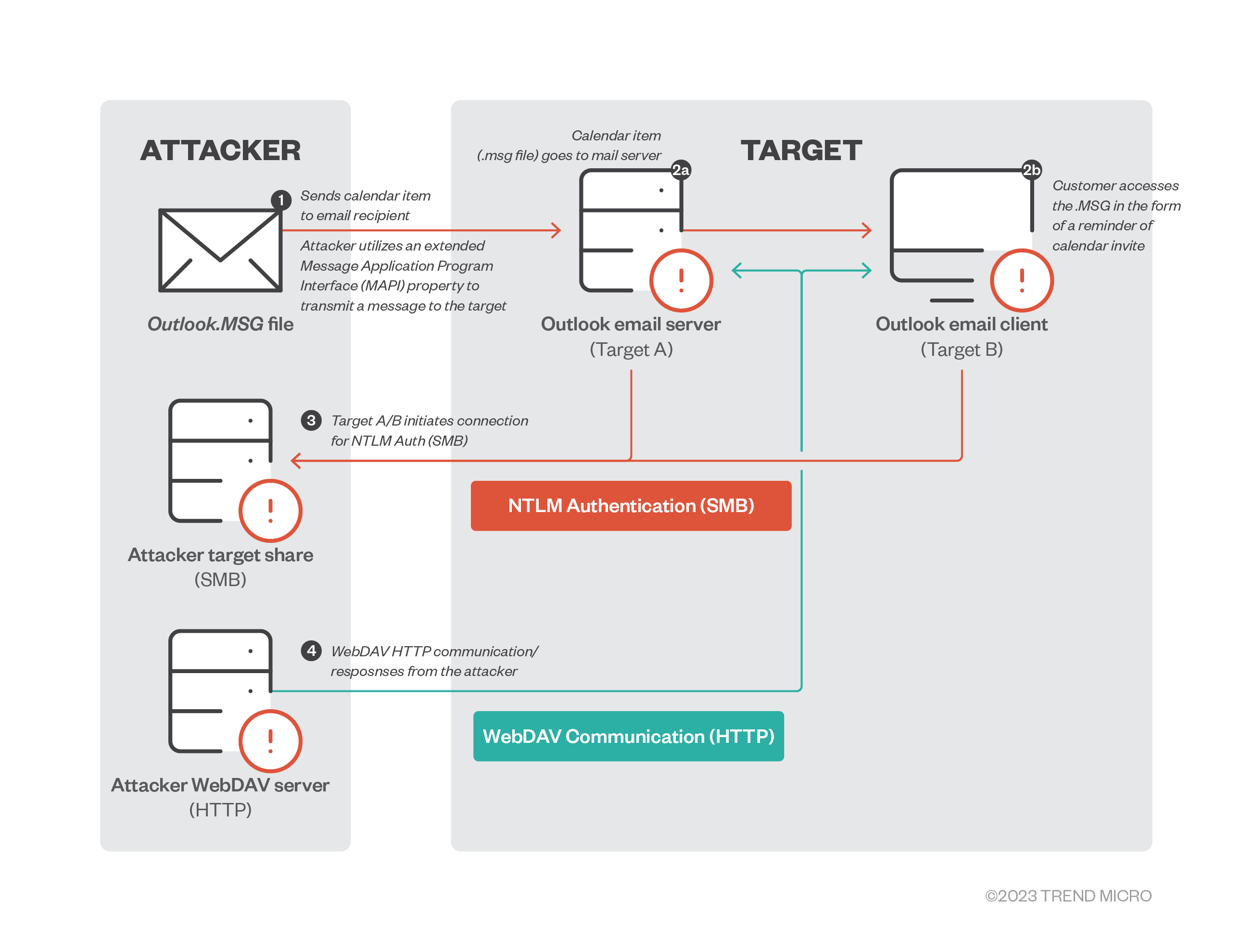
Patch CVE-2023-23397 Immediately: What You Need To Know and Do
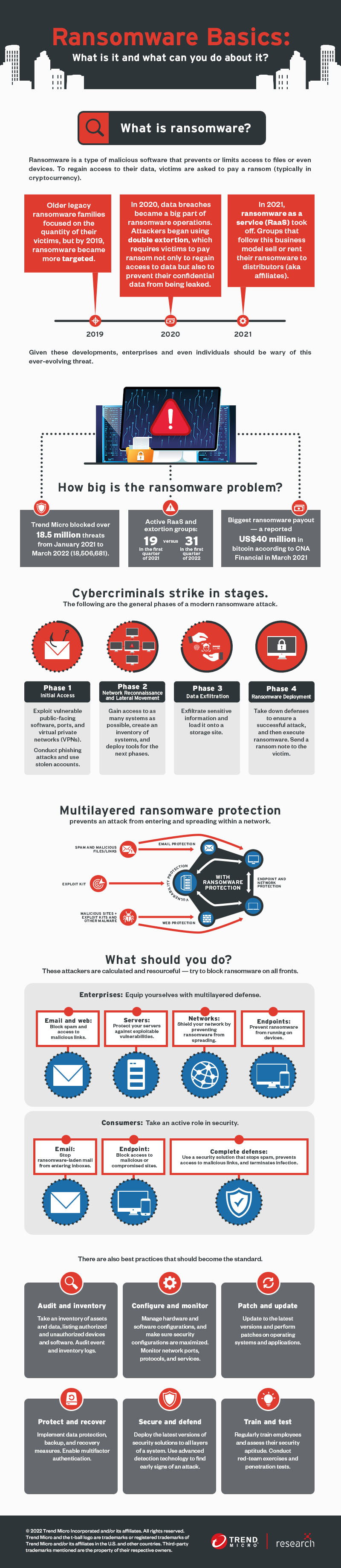
Ransomware - Definition

Crossing the Line: Unit 42 Wireshark Quiz for RedLine Stealer

Trend Micro Antivirus+ Security Review
Collecting debug logs - Portable Security 3.0
1 in Cloud Security & Endpoint Cybersecurity
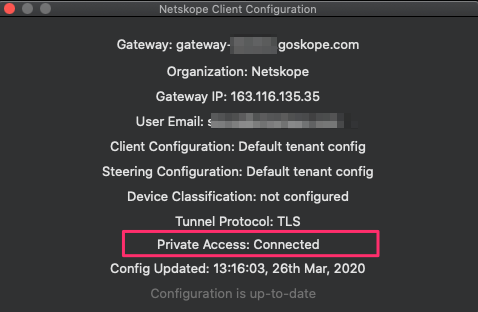
General Troubleshooting Methods - Netskope Knowledge Portal

Trend Micro Deep Security 9.5 ( DSM ) -Part 1

Top 10 Data Loss Prevention Software
Collecting debug logs - Portable Security 3.0
de
por adulto (o preço varia de acordo com o tamanho do grupo)