The loophole that file managers were using to get access to
Por um escritor misterioso
Descrição
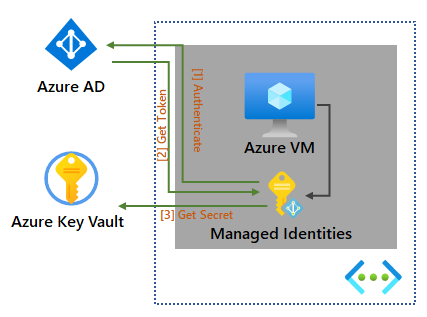
Steal Secrets with Azure Instance Metadata Service? Don't Oversight Role-based Access Control, by Marcus Tee, Marcus Tee Anytime

Not 62? Deemed filing Social Security loophole has closed

How closing the violent misdemeanor loophole could curb gun violence - ABC News

How to choose GRC Software/Tools? - Scrut Automation

10 Best Practices for Remote Work Access Security - V2 Cloud

9 Tips for Efficient Expenditure Management

Office 365 Config Loophole Opens OneDrive, SharePoint Data to Ransomware Attack

Closing the last loophole for unhackable quantum security

US agencies buy vast quantities of personal information on the open market – a legal scholar explains why and what it means for privacy in the age of AI

Closing the Loophole: Effects of Apple's New Advanced Data Protection for iCloud – Journal of High Technology Law

10 Best Vulnerability Management Tools - 2023
de
por adulto (o preço varia de acordo com o tamanho do grupo)






