How hackers use idle scans in port scan attacks
Por um escritor misterioso
Descrição
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.

Nmap cheat sheet: From discovery to exploits, part 2: Advance port scanning with Nmap and custom idle scan

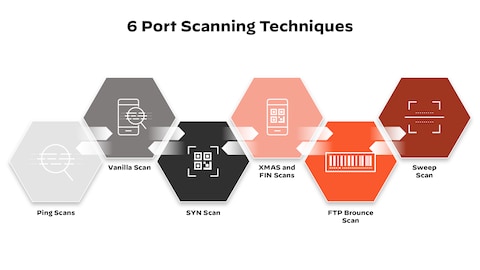
Module 3 Scanning

Scanning Techniques (EC-Council) EC-Council. Certified Ethical Hacker (CEH) Version 10 eBook w/ iLabs (Volumes 1 through 4). EC-Council Academia, 08/2018. VitalBook file. Flashcards
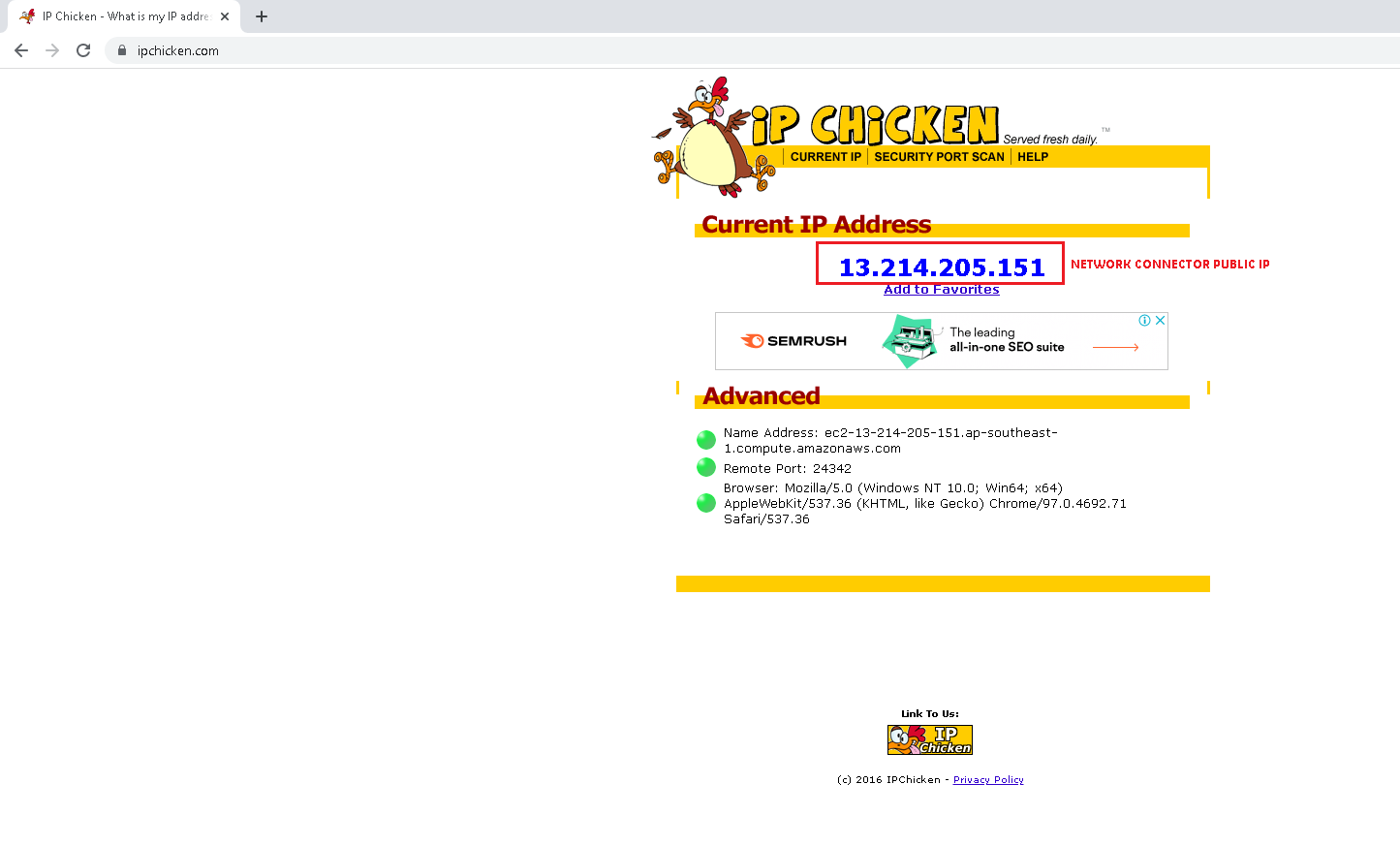
What Is Nmap? A Comprehensive Tutorial For Network Mapping

NMap > Penetration Testing and Network Defense: Performing Host Reconnaissance
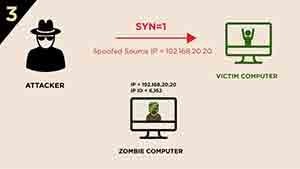
What is Idle Scan? ICterra Information and Communication Technologies
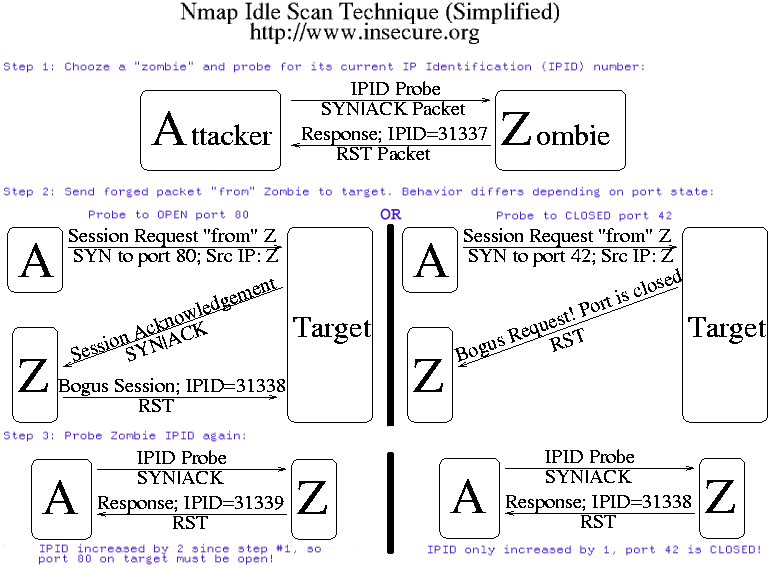
Idle Scanning and related IPID games

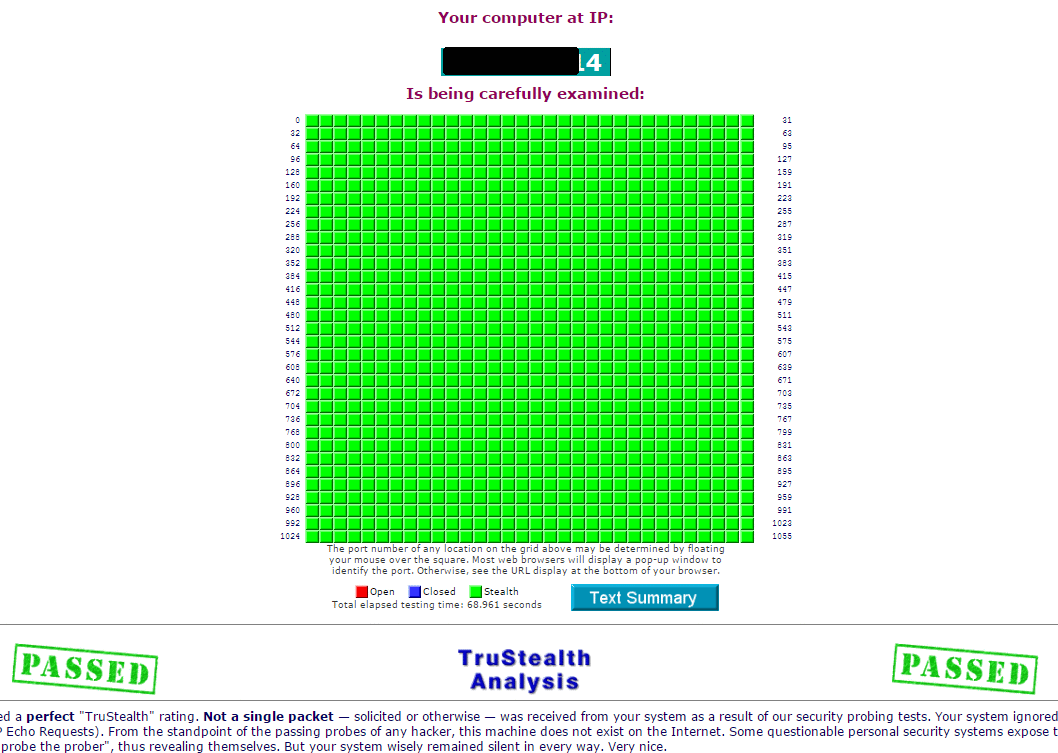
How to perform TCP connect scan (-sT) - Port scanning tutorial
What is Idle Scan? ICterra Information and Communication Technologies
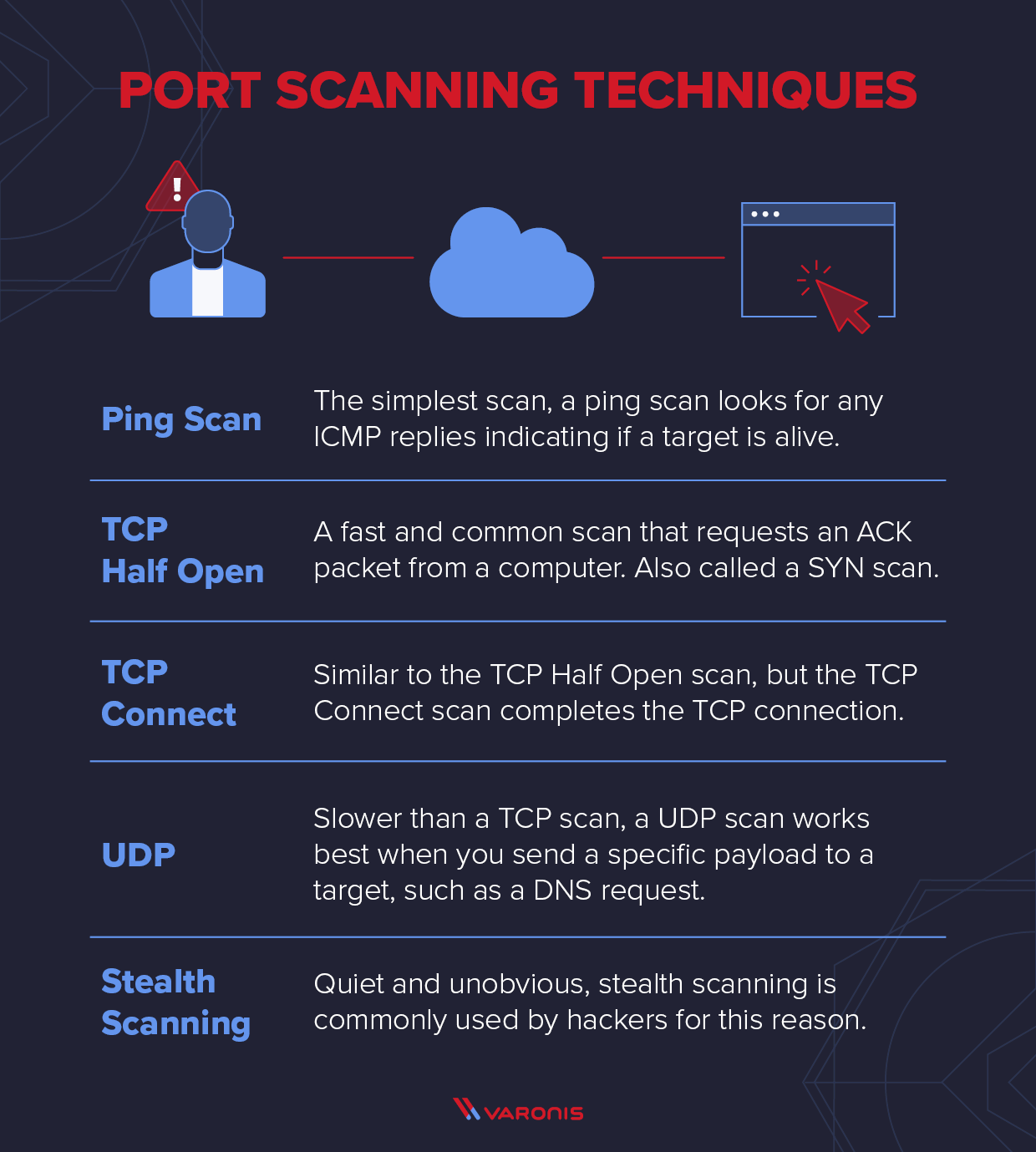
What is a Port Scanner and How Does it Work?
What is a Cyber Attack? Definition and Related FAQs

What Is an Idle Scan? (with pictures)
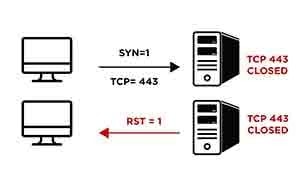
What is Idle Scan? ICterra Information and Communication Technologies
de
por adulto (o preço varia de acordo com o tamanho do grupo)