Abusing Exceptions for Code Execution, Part 1
Por um escritor misterioso
Descrição
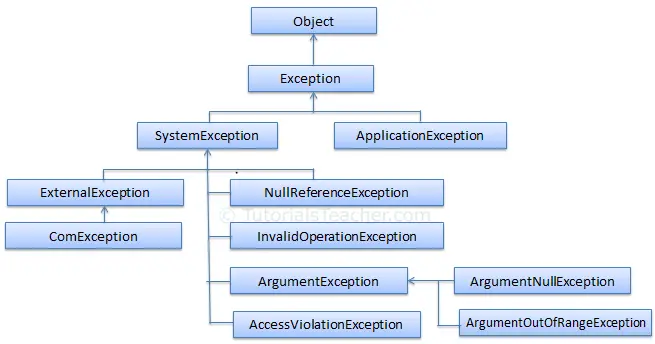
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.

Project Zero: Injecting Code into Windows Protected Processes using COM - Part 2

Loophole Abuse - TV Tropes

Top Spring Framework Mistakes

How to Fix a Toxic Culture

MSMQ QueueJumper (RCE Vulnerability): An In-Depth Technical Analysis
Smallscript - A Smalltalk-Inspired Scripting Language - CodeProject

What is code injection?, Tutorial & examples

Routing and storage overview, Cloud Logging

How Dare They Peep into My Private Life?”: Children's Rights Violations by Governments that Endorsed Online Learning During the Covid-19 Pandemic
Abusing Exceptions for Code Execution, Part 1

Arbitrary Code Execution - an overview

InnoGear Boom Arm Microphone Mic Stand for Blue Yeti HyperX QuadCast SoloCast Snowball Fifine Shure SM7B and other Mic, Medium : Musical Instruments

What are Code Smells in Angular?. In one of my previous post I talked…, by Robert Maier-Silldorff
Sample Terms of Use Template and Guide - Termly
de
por adulto (o preço varia de acordo com o tamanho do grupo)