Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Descrição
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this

HackMD - Collaborative Markdown Knowledge Base

0xdf hacks stuff CTF solutions, malware analysis, home lab
portswigger/README.md at master · roberson-io/portswigger · GitHub

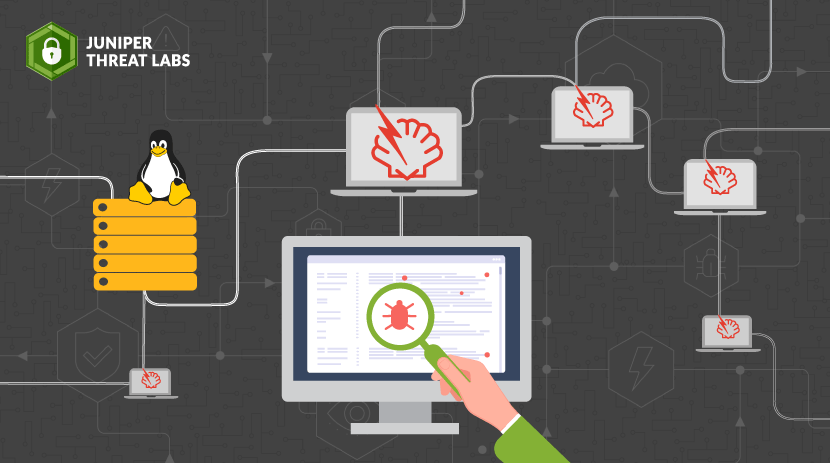
Portswigger Web Security Academy Lab: Blind SSRF with Shellshock

Blind SSRF with Shellshock exploitationをやってみた - Shikata Ga Nai
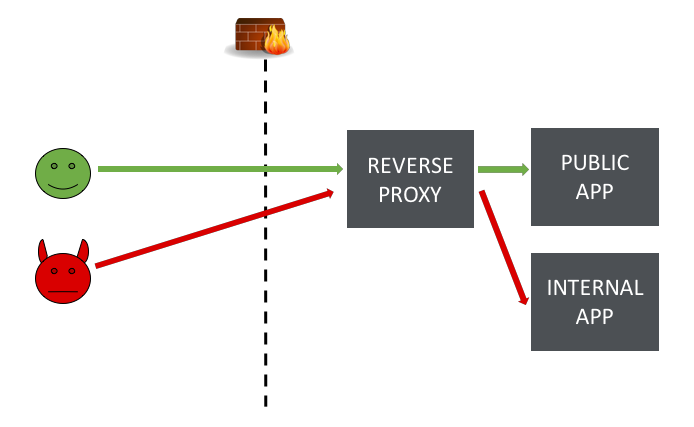
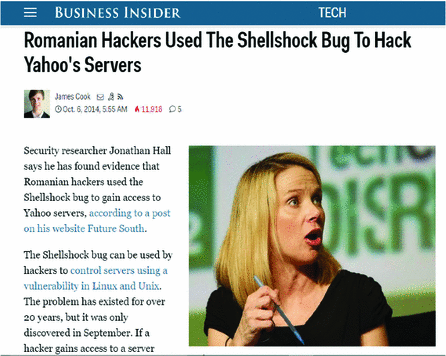
Cracking the lens: targeting HTTP's hidden attack-surface
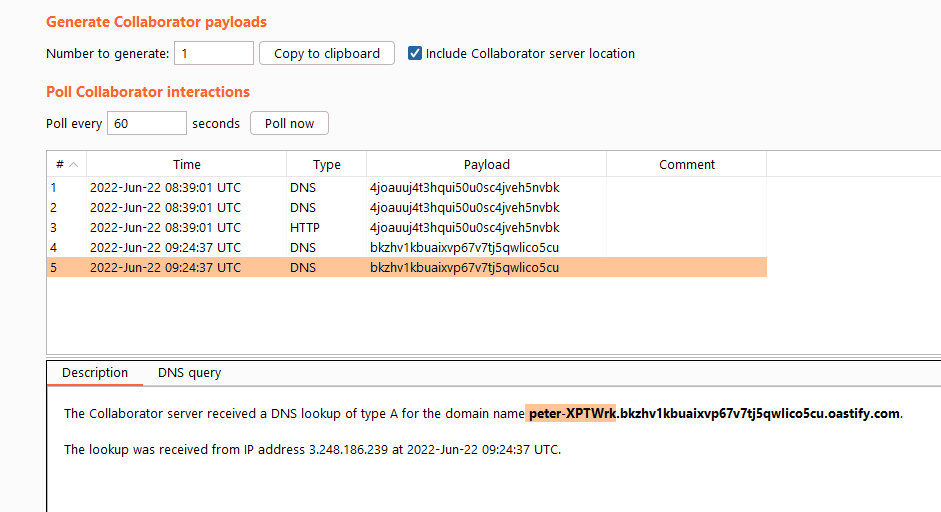
Web Application Hacking - Server-Side Request Forgery

Blind SSRF with Shellshock exploitation (Video Solution)
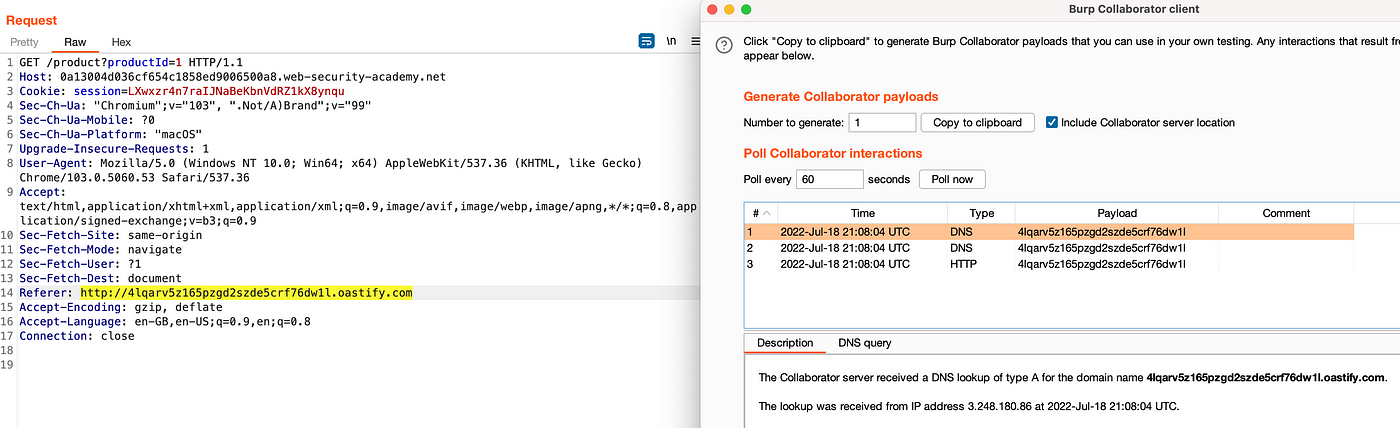
PortSwigger SSRF Labs. Hey all! This write-up is about my…

A GUIDE TO SERVER SIDE REQUEST FORGERY(SSRF) » Securityboat
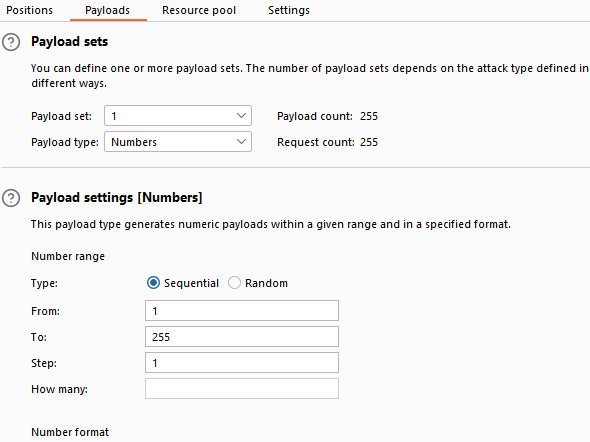
Portswigger Web Security Academy Lab: Blind SSRF with Shellshock
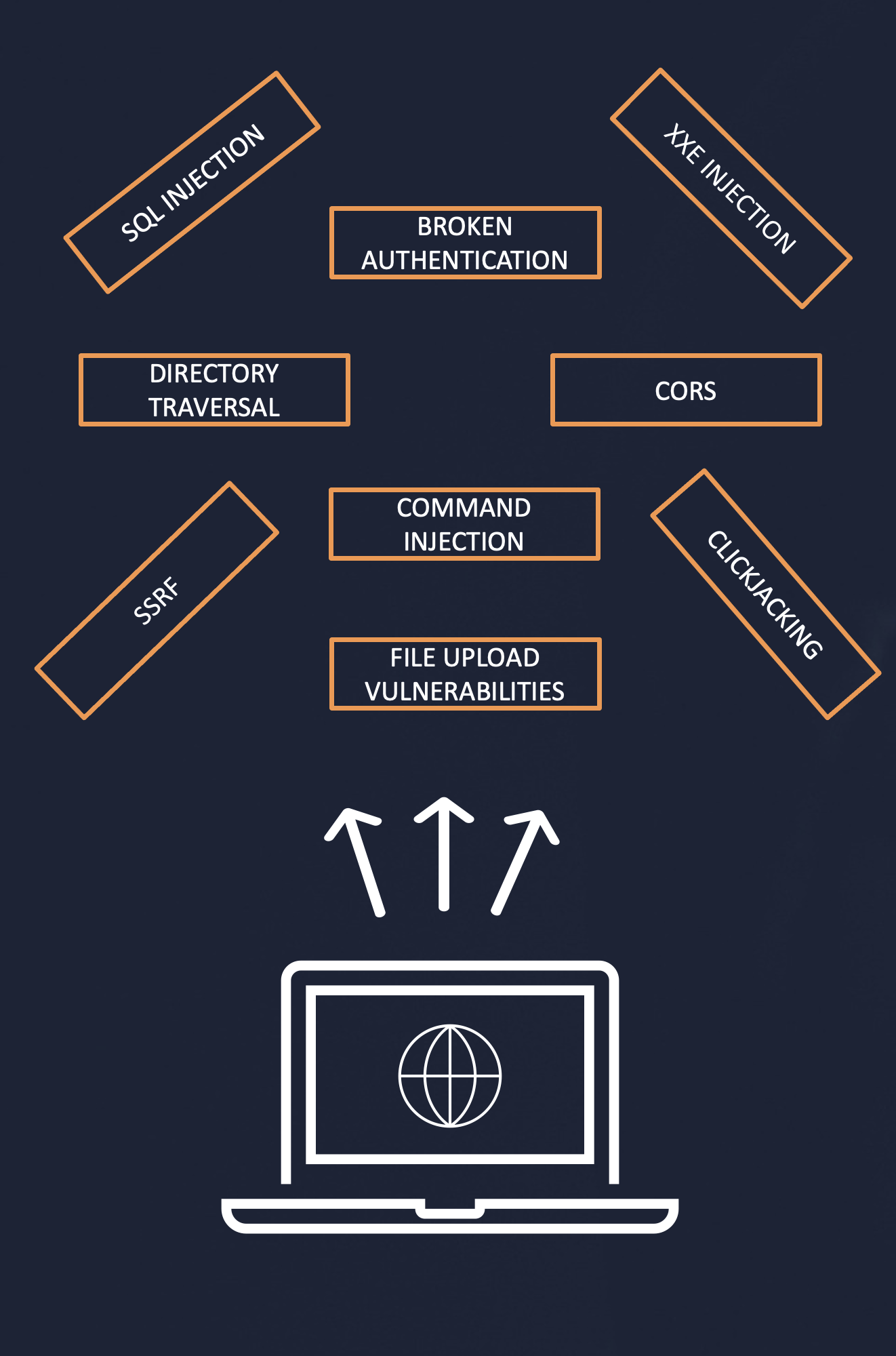
Web Security Academy Series Course
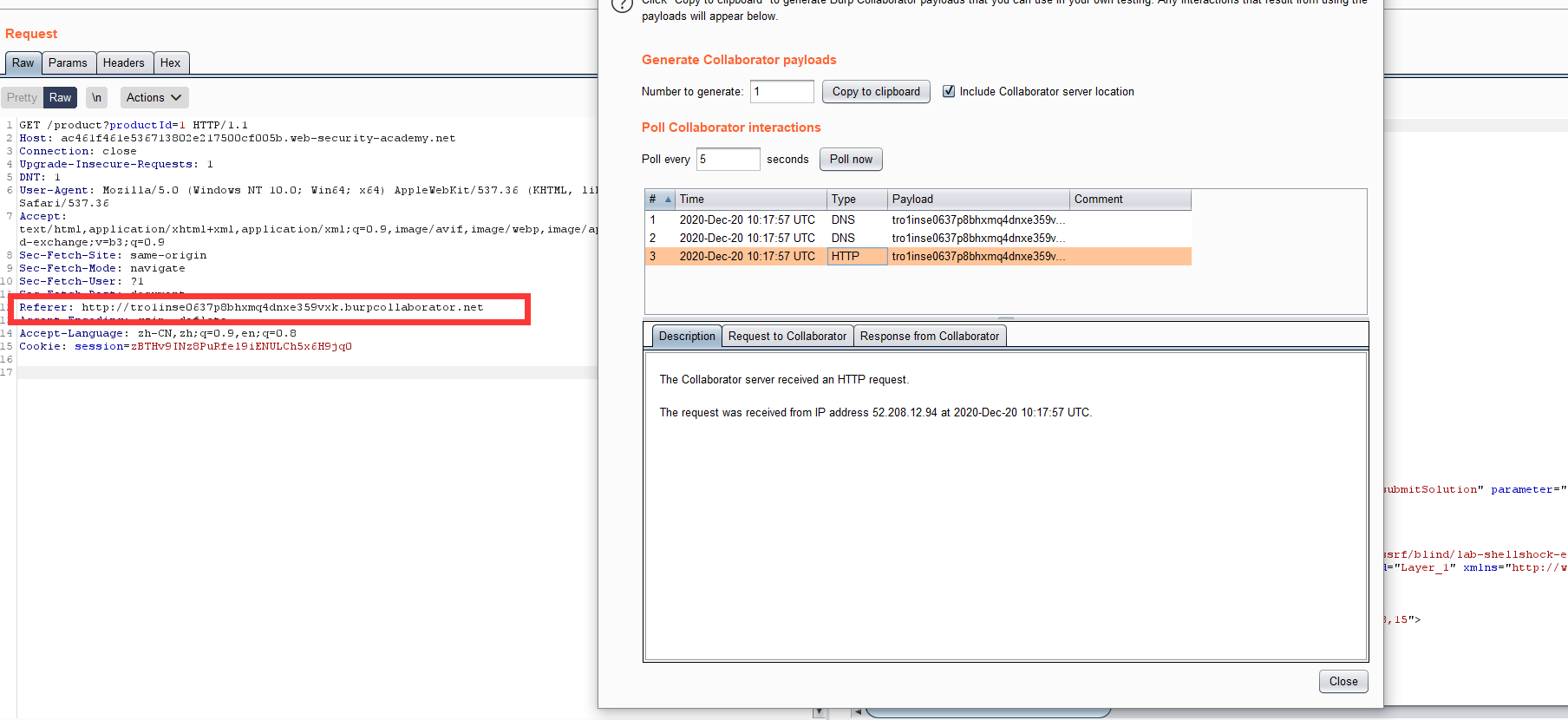
Portswigger web security academy:Server-side request forgery

Vivek Bhuria - Pune, Maharashtra, India

Blind SSRF with Shellshock exploitation (Video solution)
de
por adulto (o preço varia de acordo com o tamanho do grupo)